Application Continuity Using F5 | Part 2 | F5 Load Balancer
This is the second of a two-part series on F5 Load Balancer. In the first post, I addressed to what is Load Balancer, Its importance and its types – referred to local load balancing and global load balancing. This second part will focus on F5 Load Balancer.
Now, let’s first start with, “What is this F5?” and “What is the purpose of Load Balancer?”
So, F5 Networks, Inc. is a global company that major in application delivery networking (ADN) and application services. F5 technologies focus on the security, delivery, performance, and availability of web applications. It also focusses on the availability of servers, data storage devices, cloud resources, and other networking components.
F5 technologies are available in the data center and the cloud, including public, private, and multi-cloud environments based on platforms such as Microsoft Azure, AWS, Google Cloud Platform (GCP), and OpenStack.
F5 is originally known for its load balancing products. These days F5 products and services go beyond the delivery of applications with DNS based global load balancing and acceleration, local load balancing and acceleration to the web application firewall(WAF) for application authentication and security, anti-malware, anti-phishing and anti-fraud solutions, cloud-based DDoS mitigation services, etc.
A load balancer is a device that operates as a reverse proxy and spread out network or application traffic across several servers. Load balancers are used to increase reliability and capacity means simultaneous access to concurrent users of applications. They improve the in general performance of applications and services by decreasing the load on servers associated with maintaining and managing application and network sessions. It also performs application-specific tasks to get better application performance.
For Free, Demo classes Call: 7798058777
Registration Link: Click Here!
Load balancers are generally classified into two types: Layer 7 and Layer 4. Layer 7 i.e. Application layer load balancers allocate requests based upon data found in application layer protocols such as HTTP. Layer 4 load balancers perform upon data found in transport and network layer protocols (TCP, UDP, IP, FTP).
Client requests received on both types of load balancers are distributed to a particular server based on the algorithm configured on the load balancer. Following are some of the industry-standard algorithms are:
- Round-robin
- Least connections
- Least response time
- Weighted round-robin
Load balancers ensure availability and reliability of service, by monitoring the “health” of servers and applications and only sending requests to servers and applications which can responding in a timely manner.
In the upcoming section, we are going to see that “What F5 product is used for Load Balancing?” and “What are various features of it?”
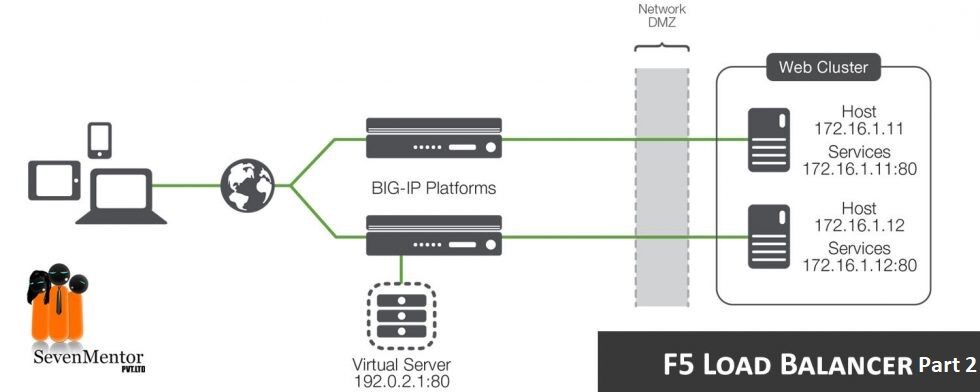
F5’s launched its first product in 1997, was a load balancer called BIG-IP. When a server in the pool unavailable or crash or became overloaded, BIG-IP give directions to that server’s traffic away from it, towards other servers in the pool that could handle the load. F5’s BIG-IP product family includes modularized software, hardware, and virtual appliances that run the F5 TMOS operating system. Depending on the appliance selected, you can add one or more BIG-IP product modules in your organisation. Various modules offered are as below:
- Local Traffic Manager (LTM): Provides Local load balancing based on a full-proxy build up structure.
- Application Security Manager (ASM): This is a web application firewall (WAF) that provides security and application authentication.
- Access Policy Manager (APM): This module provides HTTP and HTTPS application’s access control and authentication.
- Advanced Firewall Manager (AFM): This is advance data centre firewall which provides on-premises DDoS protection.
- Application Acceleration Manager (AAM): IT accelerates application performance using technologies such as caching and compression.
- IP Intelligence (IPI): This module provides protection by preventing phishing attacks and botnets, blocking known bad IP addresses.
- WebSafe: Detecting client-less malware, ability to analyse session behavioural, provides protection against sophisticated fraud threats, utilizing advanced encryption.
- BIG-IP DNS: This is nothing but the Global Traffic Manager (GTM) that provides Global load balancing. Now it is known as BIG-IP DNS. IT distributes application and DNS requests based on network, user, and cloud performance conditions.
As we can see the LTM & DNS/GTM modules are powerful tools in the world of Load Balancing and reliable Application Delivery. Together the LTM & DNS/GTM make one most efficient Application Delivery machine.
Local Traffic Manager (LTM) Outline
The Local Traffic Manager (LTM) is the most popular module offered on F5 Networks BIG-IP platform. The real power of the LTM is it’s a Full Proxy, allowing you to increase client and server side connections, while making load balancing decisions on performance, availability, and persistence. IN LTM “Local” indicate that, usually the servers in the load balancing pool be placed “locally” in the same data center.
The Virtual IP or VIP, is the main configuration element on an LTM. VIPs associate to the URL you’re load balancing, but at its lowest level i.e. locally. VIP usually contains a pool with the servers it’s load balancing & monitor(s) to measure performance and availability of servers and applications.
Global Traffic Manager (GTM) Outline
The Global Traffic Manager (GTM) which is now referred to DNS, is one of the forward-looking modules offered on F5 Networks BIG-IP platform. You can think of the GTM as an intelligent DNS that is guarded security means its’ logic can resolve the hostname to an IP address and also keeps security in check. This DNS module has the ability to make name resolution load balancing decisions for systems located anywhere in the World, like India, US, UK, etc. Hence “Global” is the right word for this BIG-IP DNS module.
The Wide IP or WIP, is the main configuration element in a GTM. A WIP associate to the common URL you’re load balancing, for example, www.sevenmentor.com. A WIP is associated with a pool or pools which contain the IPs it’s smartly resolving. The GTM does not provide any information about ports, but the monitors associated with the pool members can in reality monitor performance or availability on ports.
For Free, Demo classes Call: 7798058777
Registration Link: Click Here!
Some of the Significant differences of the LTM vs GTM
- As mentioned earlier, the biggest difference between the LTM and GTM, is traffic doesn’t actually flow through the GTM to your servers.
- When traffic is pointed towards the LTM, that traffic transfers directly through its full proxy architecture to the servers in the load balancing pool.
- The LTM does not do any name resolution and pretends that a DNS decision has already been made.
- The GTM is a cunning name resolver as it intellectually resolving hostnames to IP addresses.
- You are done with the GTM, once it provides you with an IP to route to. It will again work for you when you ask it to resolve another name for you.
- Like to a normal DNS server, the GTM also does not provide any port information in its resolution.
- As the LTM is a full proxy it is easy for it to listen on one port. Although it direct traffic to multiple hosts listening on any specified port.
How do the LTM & GTM work together?
The LTM and GTM can work together or they can be totally stand-alone. If your organization has both modules it’s usually using them jointly, and that’s where the actual potential comes in….
When in an organisation, a GTM has LTMs as servers in its’ configuration, there is no necessity to monitor the actual VIP(s) with application monitors, as the LTM is doing that. They do this using a proprietary protocol called iQuery, that functioning on TCP port 4353. Then, the VIPs that are live on LTM(s) can be dynamically resolve by the GTMs. iQuery reports VIP performance / availability back to the GTMs.
F5 BIG-IP Load Balancing Methods
The following are the basic load balancing methods whether you are load balancing two servers or scaling on-demand instances across the clouds.
Static and Dynamic Load Balancing
The first method, Static load balancing does not use any traffic metrics from the node or pool member to distribute the traffic among Servers.
While the Dynamic load balancing methods like “Least Connections” or “Least Sessions” DO use traffic metrics from the node or pool members to distribute the traffic.
Performance-based load balancing methods
There are some dynamic load balancing methods that depend on performance monitors. Performance monitors measure the hosts’ performance and send it to the dynamic load balancing methods they are working with. They used this as a matric and depending on them dynamically send more or less traffic to hosts in the pool.
Load Balancing with the F5 BIG-IP LTM
| Method | Explanation |
| Round Robin | Round Robin method is the default load balancing method. It forwards each new connection request to the next server in the pool, ultimately distributing connections evenly across the pool of servers being load balanced. |
| Ratio | For this you need to set a ratio weight when you are adding each pool member or node. Then the F5 BIG-IP system will distribute new connections among pool members or nodes in a static rotation according to ratio weights defined by you. |
| Dynamic Ratio | For this method you must first install and configure the appropriate server software and performance monitor on the pool servers. This method selects a server based on the ratio weights that are system-generated. The values of the ratio weights are dynamic as they are based on the performance monitoring of servers. |
| Fastest | The Fastest method select a server based on the least number of current requests that have not received any response. |
| Least Connections | The Least Connections methods, a new connection passes to the pool member or node that has the least number of active connections. |
| Weighted Least Connections | The Weighted Least Connections methods select pool members or nodes based on the number of active connections and the server capacity also. |
| Observed | The Observed method uses an algorithm that calculates a dynamic ratio value based on the number of Layer 4 connections last observed for each pool member and used this ratio to distribute connections among available pool members. |
| Predictive | In this method servers are rated called ranking of server according to the number of current connections. The BIG-IP system analyses the ranking over time, is it currently improving or falling. The servers that are currently improving, receive more connections. |
| Least Sessions | The Least Sessions method uses persistence table entries. Persistence entries permit the recurring clients to bypass load balancing and connect directly to the server to which they last connected. This method selects the server that currently has the least number of entries in the persistence table. |
| Ratio Least Connections | For this Ratio Least Connections method, the ratio of the number of connections that each pool member has active is calculated. According to this ratio, the BIG-IP system selects the pool member. |
For Free, Demo classes Call: 7798058777
Registration Link: Click Here!
Well, this is end of the two part series on F5 Load Balancer . I hope now you have clear idea about the need and importance of load balancing and also about F5 BIG-IP load balancer’s different features.
Tags:
- #Cisco
- Networking
- F5
- BIG-IP
- Load Balancing
- LTM
- GTM
Author Name: Sumaiyya Suhail Bagwan
Department Name: Networking
Designation: Technical Trainer
Call the Trainer and Book your free demo Class for now!!!
© Copyright 2019 | Sevenmentor Pvt Ltd.