About Cyber Security Analyst
In today’s interconnected digital environment, the importance of cybersecurity has grown exponentially. As organizations across Australia strive to protect sensitive data and critical infrastructure from cyberattacks, the demand for skilled cybersecurity analysts is at an all-time high. A Cyber Security Analyst provides professionals and aspiring analysts with the knowledge, techniques, and tools required to safeguard networks and respond to incidents effectively. In this article, we delve into the significance of Cyber Security Analyst Classes in Australia, the curriculum, the benefits of enrolling, and why SevenMentor stands out as the premier institute for training in this field.
The Importance of Cybersecurity Skills in Australia
As a pioneer in digital transformation, Australia is increasingly threatened by highly skilled cybercriminals. Because of the significant investments being made in cybersecurity projects by both the public and private sectors, qualified analysts are essential. In order to detect vulnerabilities, keep an eye out for network breaches, and put policies in place to stop unwanted access, cybersecurity analysts are essential.
The growing need for such professionals has led to the development of specialized Cyber Security Analyst courses in Australia like SevenMentor, which address the unique challenges of the Australian digital ecosystem while also aligning with global best practices. These programs prepare participants to tackle threats like phishing, malware attacks, ransomware, and insider threats, equipping them with both theoretical knowledge and hands-on experience.
What Does the Cyber Security Analyst Include?
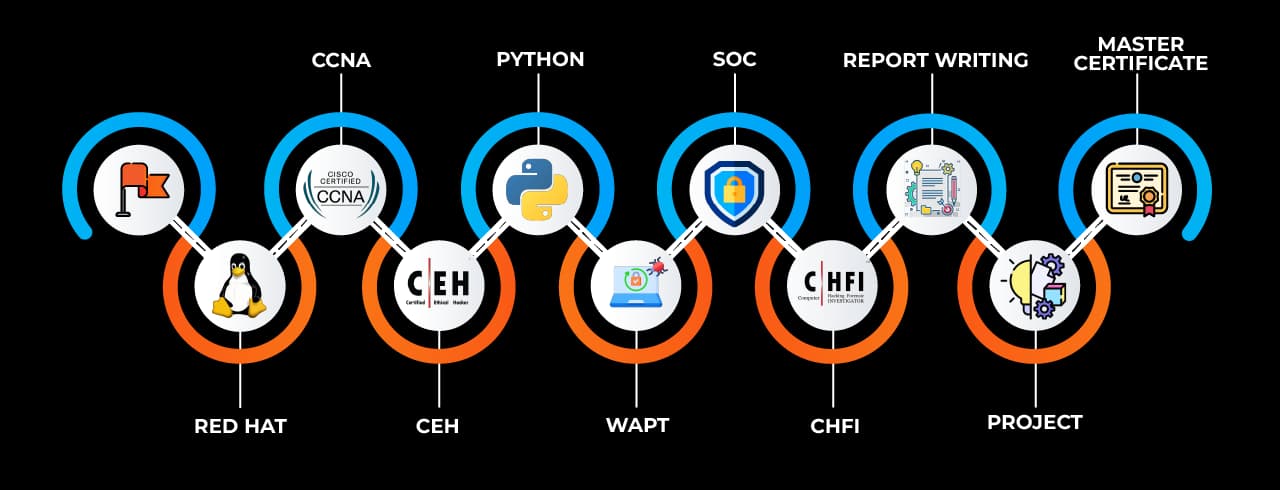
The Sevenmentor’s Cyber Security Analyst training in Australia is designed to provide an in-depth understanding of core cybersecurity concepts as well as practical exposure.Fundamentals of network security, threat analysis, incident response, vulnerability management, ethical hacking, cryptography, and compliance requirements are all topics that are usually covered in a well-structured program.
Additionally, participants learn how to evaluate threat intelligence, employ cutting-edge cybersecurity tools, and create response plans for possible attacks. Simulating real-world situations where students react to attacks in a controlled setting is a crucial part of this kind of training. That way, when they finish, they'll be prepared for the workforce. The curriculum is frequently revised to take into account new security technologies and emerging dangers, guaranteeing that students acquire current, applicable skills.
Benefits of Enrolling in Cyber Security Analyst Classes
Enrolling in Cyber Security Analyst Classes in Australia at SevenMentor offers numerous benefits for individuals and organizations alike. Students gain expertise that is both practical and globally recognized, which opens doors to a variety of career paths in cybersecurity.
Because of the mentorship and organised learning pathways offered by these seminars, professionals with non-technical backgrounds can also transfer into cybersecurity employment. On the other side, businesses gain from having internal security experts who can quickly detect and address risks, lowering the possibility of expensive breaches and data loss.
The collaborative learning environment is an additional benefit. Through interactions with seasoned instructors and peers from many industries, students can learn from real-world experiences and develop a professional network that will serve them well in their future employment.
Why Choose SevenMentor for Cyber Security Analyst Training?
Among the many training providers in the country, SevenMentor the best training institute for Cyber Security Analyst Training, has emerged as a trusted name. The institute offers cutting-edge facilities, experienced trainers, and a curriculum designed in consultation with industry leaders.
SevenMentor guarantees that students acquire substantial practical experience with real-world circumstances in addition to understanding cybersecurity theory. Thousands of students have found fulfilling careers in cybersecurity thanks to their emphasis on hands-on learning, mentorship, and career support.
SevenMentor offers the best advice and tools to help you reach your objectives in the cybersecurity space, regardless of whether you are a recent graduate hoping to get your start in the industry or an experienced expert trying to advance your abilities.
Career Opportunities After Completing the Program
Upon completing Cyber Security Analyst training in Australia at SevenMentor, graduates can explore a diverse range of career opportunities. Common job titles include cybersecurity analyst, threat intelligence analyst, SOC (Security Operations Center) analyst, vulnerability assessor, and incident response specialist.
These positions are highly sought after in a variety of industries, including technology, retail, government, healthcare, and finance. To further improve their employability, professionals with cybersecurity expertise can also work towards certifications like CompTIA Security+, Certified Ethical Hacker (CEH), or CISSP.
Due to Australia's dedication to bolstering its cybersecurity posture, employment opportunities for skilled analysts are expected to increase over the coming years, offering exceptional career stability and room for advancement.
The Structure and Delivery of the Classes
Cyber Security Analyst Classes in Australia at Sevenmentor are structured to cater to different learning preferences and schedules. Programs may be offered as full-time, part-time, weekend, or evening classes, making them accessible to working professionals as well.
Lectures, debates, practical laboratories, and project work are all common components of classroom sessions. To mimic actual attacks and defences, several institutions also use cyber range exercises and mock drills. In order to determine students' development and preparedness for industrial responsibilities, the curriculum includes assessments, quizzes, and practical tests.
This well-rounded curriculum guarantees that students acquire the practical problem-solving abilities necessary for cybersecurity professionals in addition to the academic underpinnings.
Technologies and Tools Covered
The Cyber Security Analyst courses in Australia at Sevenmentor introduce participants to a range of cybersecurity tools and technologies used in the industry. These include intrusion detection systems (IDS), firewalls, security information and event management (SIEM) tools, penetration testing software, and threat intelligence platforms.
Students become familiar with popular tools such as Wireshark, Nessus, Metasploit, and Splunk, and learn to use these tools to monitor, detect, and respond to security incidents effectively. The hands-on exposure to such tools is invaluable, as it builds confidence and proficiency, enabling students to handle real-life cybersecurity challenges with competence.
Adapting to the Evolving Threat Landscape
Cybersecurity is a dynamic field where threats evolve constantly. Hence, training programs must adapt accordingly. The Cyber Security Analyst Classes in Australia offered bySevenMentor emphasize continuous learning and staying updated with emerging trends.
Topics like cloud security, IoT (Internet of Things) security, and AI-driven threats are increasingly incorporated into the curriculum. Students also learn about evolving compliance requirements such as the Australian Privacy Principles (APPs) and international regulations like GDPR, which are critical for organizations operating globally.
The Cyber Security Analyst Classes in Australia are a gateway to building a rewarding career while contributing to the security and resilience of digital infrastructures. With a comprehensive curriculum, hands-on training, and expert guidance, these programs prepare students to tackle real-world challenges with confidence and competence.
For those seeking high-quality, industry-relevant training, SevenMentor the best training institute for Cyber Security Analyst Training stands out as the preferred choice. Their commitment to excellence, practical learning approach, and proven track record make them an ideal partner in your journey towards becoming a skilled cybersecurity analyst.
Online Classes
SevenMentor also offers comprehensive online Cyber Security Analyst Classes in Australia are also available online. Online training offers the same comprehensive curriculum and expert guidance as traditional in-person classes, but with the added advantage of learning from anywhere.
Students can attend live instructor-led sessions, participate in virtual labs, and access recorded materials for revision at their own pace. Online platforms also provide discussion forums and direct communication channels with trainers, ensuring that learners remain engaged and supported throughout the program.
Corporate Training
Sevenmentor offers specialized corporate Cyber Security Analyst training in Australia tailored for corporate clients. Corporate training is customized to align with the specific security needs and policies of the organization. It can be delivered on-site or virtually, ensuring minimum disruption to daily operations. Employees are trained on relevant technologies, threat scenarios, and compliance requirements pertinent to their industry.
By investing in corporate training, companies not only strengthen their security posture but also empower employees with skills that boost productivity and morale. With the expertise of SevenMentor, the best training institute for Cyber Security AnalystTraining, organizations can be assured of impactful and result-oriented corporate training solutions.
 A cybersecurity analyst safeguards an organization's networks, hardware, and software from cyberattacks while also ensuring the security of the organization's information systems.
A cybersecurity analyst safeguards an organization's networks, hardware, and software from cyberattacks while also ensuring the security of the organization's information systems. An information security analyst would also think about the security of data housed elsewhere, such as records in an archive or insider information held by some employees.
An information security analyst would also think about the security of data housed elsewhere, such as records in an archive or insider information held by some employees. The SevenMentor Cyber Security Analyst Course has classes that explain cyber attacks, malware, and hackers' behaviours.
The SevenMentor Cyber Security Analyst Course has classes that explain cyber attacks, malware, and hackers' behaviours.