About Cyber Security
In the age of hyperconnectivity, the role of cyber security cannot be overemphasized. With each organization – be it in finance, healthcare, education, or government – increasingly dependent on digital infrastructure, protection of this ecosystem becomes a top priority. With threats such as ransomware, phishing, data breaches, and cyber espionage becoming more advanced by the day, demand for specialists who can fight these issues is higher than ever. This has generated a pressing demand for organized, practical, and industry-focused Cyber Security Classes in Ahmednagar, enabling people to get ready to face the constantly changing cyber threat environment.
Ahmednagar, a growing educational and IT hub in Maharashtra, is fast becoming a destination for aspiring tech professionals. With increasing internet penetration and digital adoption in regional sectors, the local industry and academia have started to emphasize cyber security education. For those seeking a reliable and effective way to enter the field, SevenMentor offers comprehensive Cyber Security training in Ahmednagar that blends theoretical foundations with real-world practical implementation.
The Role of Cyber Security in Modern IT Infrastructure
Cyber security is an expansive collection of safeguards which protect computers, networks, and information from unauthorized access, invasion, and destruction. Fundamentally, cyber security is all about safeguarding confidentiality, integrity, and availability, often referred to as the CIA triad. Increased use of hybrid work patterns, mobile computing, and cloud applications has exponentially increased the attack surface, which has rendered perimeter-based security a thing of the past.
Threat actors are no longer limited to opportunistic hackers but also include state-sponsored actors, organized crime groups, and insider threats. Therefore, companies are in immediate need of experts equipped with the knowledge of ethical hacking, intrusion detection, vulnerability assessment, security compliance, and incident response. These competencies are the pillars of contemporary cyber defense, and proficiency in them demands deep, tutelage-based training like Cyber Security courses in Ahmednagar.
About SevenMentor
SevenMentor has emerged as a leading name for technology education across India. Recognized for its state-of-the-art curriculum and expert mentorship. The program offered in Ahmednagar by SevenMentor is a part of this reputable legacy, delivering instruction that meets international standards.
Unlike generic IT courses that skim the surface, the Cyber Security course at SevenMentor is developed by industry professionals who have worked in SOC (Security Operations Center), penetration testing labs, and enterprise security projects. This allows learners to gain actionable skills that are directly applicable in real-world environments. The training includes modules on network security, cryptography, ethical hacking, firewalls, SIEM tools, malware analysis, and more.
In addition to technical instruction, SevenMentor ensures that learners understand risk management and compliance frameworks like ISO 27001, NIST, and GDPR. This dual focus on technology and governance equips professionals to handle both operational and strategic aspects of cybersecurity.
Learning Outcomes and Curriculum Overview
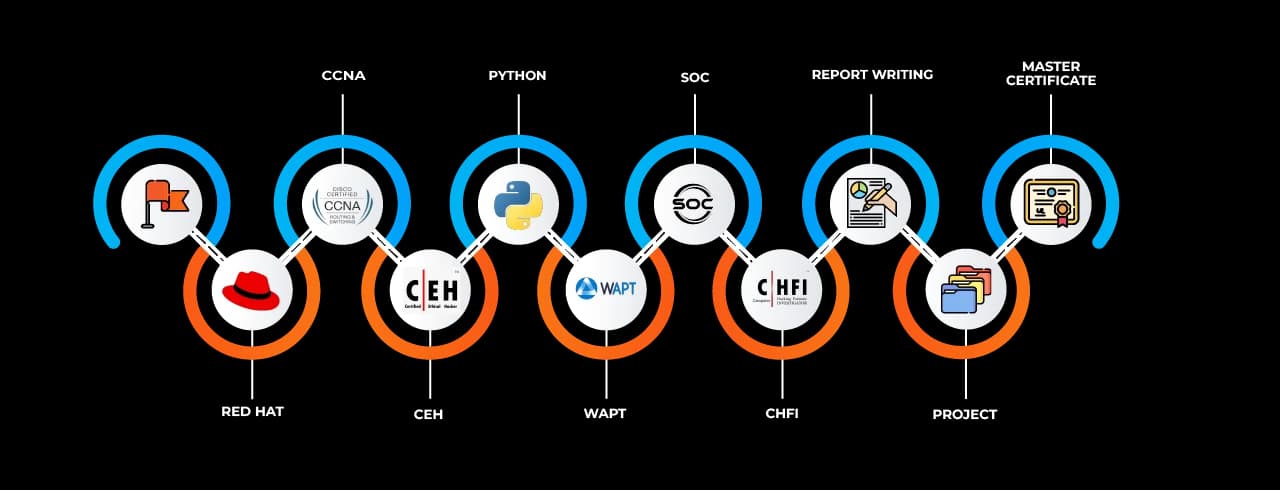
The curriculum at SevenMentor is extensive and constantly updated to reflect the latest threats, vulnerabilities, and tools in the cybersecurity domain. Students begin with the basics of networking and operating systems to ensure a solid foundation. As they progress, they delve into Linux security, Windows Active Directory exploitation, web application attacks, and wireless security.
Hands-on labs simulate real attack scenarios using tools such as Metasploit, Burp Suite, Wireshark, Nmap, Nessus, and Splunk. Learners are also trained to respond to incidents and conduct forensic investigations. The course emphasizes a red-team and blue-team approach, allowing students to both attack and defend systems in controlled environments.
A major benefit of the Cyber Security Classes in Ahmednagar offered by SevenMentor is the inclusion of capstone projects and case studies. These help learners understand how cyber-attacks unfold in actual business environments and how defense mechanisms are implemented. Additionally, students get exposure to automation tools and scripting techniques using Python and Bash, which enhances their ability to create custom solutions for unique cyber threats.
Certifications and Career Opportunities
Upon successful completion of the course, students are guided to pursue globally recognized certifications like CEH (Certified Ethical Hacker), CompTIA Security+, CISSP, and CISM. These certifications are highly valued by employers and often serve as a benchmark of competency in the field.
Industry Relevance and Practical Orientation
SevenMentor is considered the best training institute for Cyber Security Training because of its strong alignment with industry needs. The faculty members are not just academicians but active practitioners who bring current, real-time threat intelligence into the classroom. Students are taught to use the same tools and frameworks that enterprises deploy in their own IT infrastructure, giving them an authentic learning experience.
Moreover, guest lectures and workshops by CISOs and security architects provide students with valuable exposure to corporate expectations and evolving security strategies. These sessions cover recent security incidents, response measures, and lessons learned, adding depth to the academic curriculum.
Infrastructure and Learning Environment
The Ahmednagar center of SevenMentor is equipped with modern labs, high-speed internet, and simulation platforms that recreate enterprise environments. The classroom training is complemented by cloud-based labs, enabling remote access to practical exercises at any time. This hybrid approach ensures that students can continue learning outside of class hours and work on assignments in a flexible manner.
Regular assessments, mock interviews, and resume-building workshops are also part of the training, ensuring holistic development. The supportive learning community and responsive faculty make the entire training process engaging and effective for learners from all backgrounds.
Placement Support and Alumni Success
SevenMentor has a strong track record of placing students in leading organizations across India and abroad. With dedicated placement support, resume guidance, and interview preparation, students are well-equipped to face competitive hiring processes. Companies across domains including finance, healthcare, e-commerce, telecom, and government routinely recruit cyber security professionals trained at SevenMentor.
Many alumni of the Cyber Security courses in Ahmednagar have secured roles in multinational companies and continue to return to mentor new batches. This creates a valuable ecosystem of networking and continuous learning for new students.
Cyber Security Classes in Ahmednagar offered by SevenMentor provide the perfect launchpad. With a hands-on curriculum, industry-aligned modules, expert faculty, and strong placement support, students are not just educated—they are empowered. In a digital age where security is non-negotiable, the right training can make all the difference. Choose a path that leads to knowledge, growth, and protection—choose SevenMentor.
Online Course
SevenMentor offers a fully interactive online cyber security training. The Cyber Security training in Ahmednagar through the online format includes live instructor-led sessions, access to virtual labs, recorded lectures for revision, and online assessments.
What sets the online training apart is its flexibility. Learners can access the course from anywhere, without compromising on the quality of instruction or interactivity. Real-time Q&A, collaborative exercises, and 24/7 lab access ensure that remote students receive the same attention and practical exposure as classroom learners. Regular doubt-solving sessions and project evaluations keep students on track and motivated throughout the learning journey.
Corporate Training
SevenMentor provides tailored corporate Cyber Security training programs to organizations in Ahmednagar seeking to upskill their IT teams. These programs are designed after understanding the company’s existing infrastructure, security gaps, and compliance requirements.
Trainers with experience in enterprise security implementation lead these sessions, ensuring that employees are trained in real-world tools, methodologies, and best practices. Customizable modules cover areas such as endpoint protection, secure software development, cloud security, incident response, and regulatory compliance. By enrolling in SevenMentor's corporate Cyber Security courses in Ahmednagar, businesses ensure their teams are prepared to prevent, detect, and mitigate cyber threats effectively.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)