About Cyber Security
In the evolving digital ecosystem of today, the demand for robust cybersecurity infrastructure is at an all-time high. Organizations in Abu Dhabi, both private and governmental, are investing heavily in securing their digital assets from increasing cyber threats. As a result, there is a growing need for highly skilled professionals in this domain. This has led to the rise in popularity of Cyber Security Classes in Abu Dhabi, helping students and professionals acquire cutting-edge skills in information security, ethical hacking, risk assessment, cryptography, and network defense. These classes are essential for anyone looking to build a career in IT security or strengthen their technical profile in the IT sector.
The Growing Importance of Cyber Security Training in Abu Dhabi
As digital transformation continues to reshape industries, the UAE, particularly Abu Dhabi, has emerged as an important player in the digital economy. However, this expansion has its own set of problems. Cyberattacks, phishing schemes, virus incursions, and data breaches have become commonplace. Companies are recognising the value of investing not only in cybersecurity systems, but also in educated individuals who can predict, detect, and neutralise attacks in real time.
This is where Cyber Security training in Abu Dhabi gains importance. Training institutes in the city are offering comprehensive programs that cover theoretical knowledge as well as hands-on experience with modern tools and platforms. From vulnerability assessment to penetration testing, these programs are structured to develop a workforce that is both technically competent and strategically aware of cyber laws, compliance, and security frameworks.
Curriculum Overview: Building a Cybersecurity Mindset
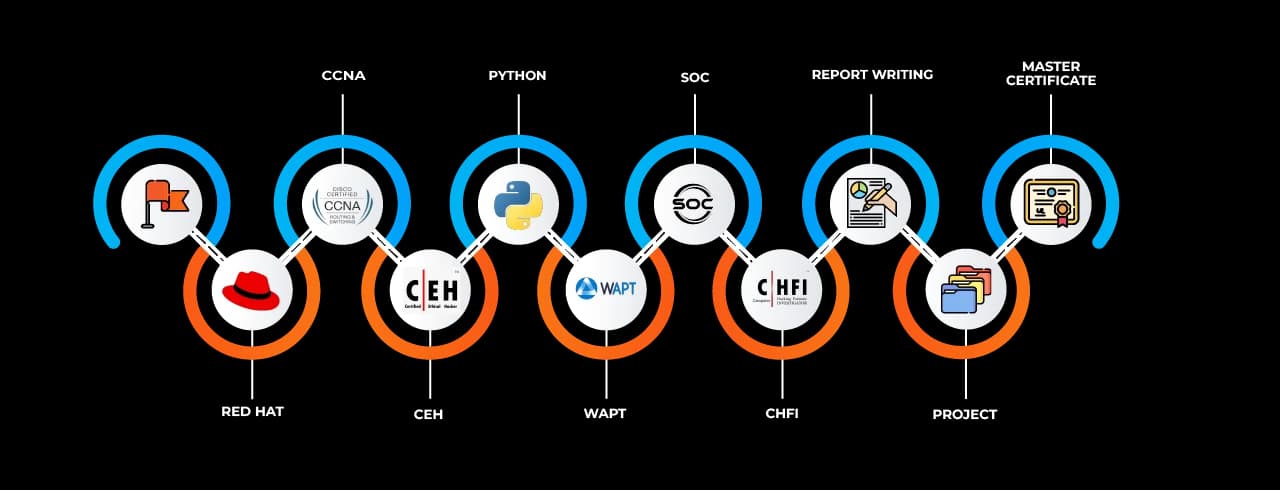
Cyber Security Classes in Abu Dhabi offered by SevenMentor are designed with industry requirements in mind. The courses begin with foundational concepts like network security, system vulnerabilities, and types of cyber threats. As the training progresses, learners are introduced to more advanced topics such as ethical hacking, security operations centers (SOC), digital forensics, cryptographic systems, and enterprise-level threat mitigation strategies.
Students can mimic real-world cyberattacks and defence mechanisms through practical lab sessions that use technologies such as Wireshark, Metasploit, Nmap, Burp Suite, Nessus, and Kali Linux. This hands-on approach instills confidence and develops understanding, preparing students for both work duties and certification exams.
In addition, the curriculum introduces students to internationally recognised frameworks including NIST, ISO 27001, and CIS Controls. Knowledge of these standards is essential, particularly in compliance-driven industries such as finance, government, and healthcare, which are prevalent in Abu Dhabi.
Industry-Relevant Certifications and Job Readiness
One of the most attractive aspects of enrolling in SevenMentor’s Cyber Security Courses in Abu Dhabi is the focus on industry certifications. Top courses are aligned with certifications such as CompTIA Security+, CEH (Certified Ethical Hacker), CISSP (Certified Information Systems Security Professional), CISM (Certified Information Security Manager), and OSCP (Offensive Security Certified Professional).
These credentials serve as proficiency standards and are recognised by businesses worldwide. Many training programs in Abu Dhabi not only educate students for these tests, but also help them schedule and complete their certification requirements.
After completing the course, students will be prepared to pursue careers as a Cybersecurity Analyst, Security Engineer, Penetration Tester, SOC Analyst, Network Security Administrator, and Information Security Consultant. With the UAE's emphasis on smart cities, AI integration, and cloud infrastructure, the demand for expertise in these fields is projected to increase.
Why Choose SevenMentor for Cyber Security Training?
SevenMentor, the best training institute for Cyber Security Training has set itself apart with its commitment to quality education and industry-relevant skills. Located strategically with access to the growing tech ecosystem of Abu Dhabi, SevenMentor combines classroom learning with practical labs and project work.
What truly differentiates SevenMentor is its focus on mentorship and continuous assessment. Each student is guided through project-based learning modules, simulation exercises, and real-time problem-solving scenarios. The faculty at SevenMentor consists of certified cybersecurity professionals with years of hands-on experience in the field. Their insights help students bridge the gap between theoretical concepts and real-world implementation.
Moreover, SevenMentor provides lifetime access to updated training material and regularly conducts mock interviews, resume building workshops, and placement drives. This holistic approach makes it the best training institute for Cyber Security Training in Abu Dhabi for students and working professionals alike.
Infrastructure and Learning Environment
The facilities at SevenMentor are designed to promote an intensive learning experience. Classrooms are equipped with the latest computers, simulation software, and secure testing environments that mimic enterprise networks. This allows learners to experiment with tools and techniques in a risk-free environment. The curriculum is kept in sync with technological advancements, ensuring that students are always learning what is most current in the cybersecurity space.
In addition to core modules, SevenMentor includes case studies from the UAE and international cyber incidents to help students understand the socio-technical impact of security breaches. This level of contextual understanding is crucial for cybersecurity professionals who will be tasked not only with defense but also with strategic risk mitigation in the real world.
Real-Time Projects and Capstone Integration
Another reason why Cyber Security Courses in Abu Dhabi stand out is the inclusion of real-time projects in the learning methodology. Projects might include designing secure network architectures, performing vulnerability scans for a mock organization, analyzing malware behaviors, or conducting red team-blue team simulations.
These capstone projects help consolidate all the technical skills acquired throughout the course and offer a portfolio that students can present to employers. Projects are reviewed by instructors and sometimes even by industry professionals who provide direct feedback, giving learners a unique opportunity to refine their approach and technical precision.
Customized Learning Paths for Beginners and Professionals
Cyber Security Classes in Abu Dhabi cater to a wide range of learners—from fresh graduates to IT professionals looking to specialize or upskill. Beginners are guided through a step-by-step learning process, while advanced learners have access to specialized modules such as reverse engineering, advanced persistent threats (APT), or IoT security.
The modular structure of courses allows students to pace their learning as per their availability and career goals. For those who already possess some knowledge or work experience, fast-track options are available, making it easier to upskill without disrupting their current professional engagements.
In a city like Abu Dhabi, which is quickly transforming into a hub of digital innovation, securing IT infrastructure and data systems is not just a necessity but a priority. Professionals trained in cybersecurity are, and will continue to be, in high demand. Whether you are a student exploring career options, a working professional aiming to switch domains, or an IT expert looking to specialize further, enrolling in Cyber Security training in Abu Dhabi is a step in the right direction.
The practical and certification-oriented approach adopted by SevenMentor, the best training institute for Cyber Security Training ensures that students are well-prepared for both the job market and real-world challenges. Through rigorous hands-on learning, mentorship, and a forward-looking curriculum, SevenMentor delivers a comprehensive learning experience that empowers students to become highly capable cybersecurity professionals.
Online Classes
SevenMentor offers comprehensive online Cyber Security training programs. These sessions are conducted in real-time by certified instructors and include live lab access, virtual simulations, and continuous mentor support. The online platform is interactive, allowing learners to engage with peers and instructors through chat, screen sharing, and problem-solving sessions.
Online training offers flexibility and is ideal for working professionals, remote learners, or those who prefer to study at their own pace. The curriculum for the online program is identical to the classroom version, ensuring consistent quality and learning outcomes. Learners also get access to recorded sessions, downloadable resources, and online assessments to track progress.
Corporate Training
SevenMentor offers tailor-made corporate Cyber Security training solutions for specific needs of businesses. Whether it's compliance training for employees, upskilling the IT department, or conducting cybersecurity audits and simulations, SevenMentor delivers impactful results.
Corporate training programs can be conducted on-site, at the company’s premises, or online for distributed teams. These programs include customized modules focusing on real-world business environments, with an emphasis on securing cloud infrastructure, endpoint security, and regulatory compliance. Through detailed assessments and practical labs, organizations can ensure that their teams are prepared to defend against evolving cyber threats.
By investing in corporate and online training options through SevenMentor the best training institute for Cyber Security Training, companies and individuals in Abu Dhabi gain access to one of the most robust and adaptable cybersecurity learning ecosystems in the region.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)