About Cyber Security
Cybersecurity is now a major worry for businesses, governments, and individuals alike in today's linked globe. All industries are seeing a sharp increase in demand for qualified cybersecurity specialists as a result of increasingly complex threats. A thorough and organised learning route is necessary for Chandrapur applicants hoping to enter this important and profitable field. The Cyber Security Job Ready Program Classes in Chandrapur offer an ideal gateway to build a successful career in cybersecurity, arming learners with the theoretical knowledge and hands-on experience necessary to combat real-world cyber threats.
Overview of Cyber Security Job Ready Program
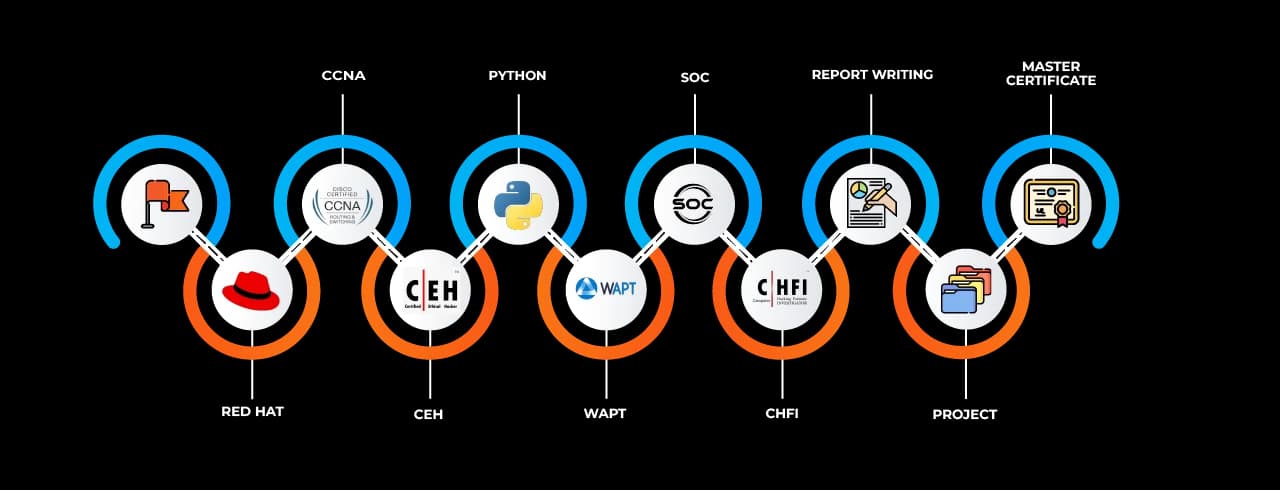
The Cyber Security Job Ready Program training in Chandrapur is a meticulously designed, industry-aligned curriculum focused on preparing learners for immediate employment in the cybersecurity sector. The course structure includes core modules on network security, ethical hacking, penetration testing, threat intelligence, incident response, cloud security, and compliance frameworks such as GDPR, ISO/IEC 27001, and more. It ensures learners are not just aware of the concepts but are also capable of implementing and managing end-to-end cybersecurity solutions.
Both professionals wishing to advance their careers and enter cybersecurity responsibilities and novices with a rudimentary understanding of IT can benefit from this training. The goal of this program is to produce individuals who are prepared for the workforce and have a thorough awareness of contemporary danger landscapes, from learning how to defend company networks to acquiring the abilities needed to manage a security breach.
Curriculum Depth and Technical Modules
The strength of the Cyber Security Job Ready Program courses in Chandrapur lies in the depth and breadth of its curriculum. Learners start with the foundational concepts of information security, including the CIA triad (Confidentiality, Integrity, Availability), types of malware, and risk management strategies. From there, they move on to advanced modules such as:
- Network Security Architecture: Students learn about secure network design, VPNs, firewalls, IDS/IPS, and VLAN segmentation. They gain hands-on practice in configuring secure network environments.
- Ethical Hacking & Penetration Testing: A core component of the course, students are taught reconnaissance, scanning, exploitation, and post-exploitation techniques using tools like Nmap, Metasploit, and Wireshark.
- Application Security: This module covers OWASP Top 10 vulnerabilities, secure coding practices, web application firewalls, and input validation techniques. Learners engage in bug bounty simulations and code analysis tasks.
- Cloud Security Fundamentals: As organizations shift to cloud platforms, securing cloud infrastructure becomes critical. This section teaches IAM, data encryption, and compliance in services like AWS, Azure, and GCP.
- Security Operations and Incident Response: Students learn how to monitor systems, detect anomalies, and respond to breaches using SIEM tools and SOC workflows.
- Compliance and Governance: The course also educates students on compliance protocols and how cybersecurity integrates with legal and business policies.
Each of these modules is paired with lab exercises, simulations, and capstone projects to ensure practical proficiency. Students graduate from this course with the ability to think like an attacker and act as a defender.
Hands-On Learning and Lab Environments
Theory without practice is insufficient in the realm of cybersecurity. The Cyber Security Job Ready Program Classes in Chandrapur at SevenMentor emphasize hands-on labs that simulate real-world attack scenarios. Learners get access to virtualized lab environments where they can test their skills safely and securely. These labs provide exposure to a wide array of tools and platforms used by professionals in the industry, including Kali Linux, Burp Suite, Nessus, Splunk, and more.
In addition to individual labs, group activities are also integrated into the program to build team collaboration skills. Learners are encouraged to conduct mock penetration tests, participate in red team-blue team exercises, and analyze breach case studies. This approach ensures a holistic learning experience and builds confidence for real-world job responsibilities.
Career Scope and Industry Demand
With the alarming rise in data breaches and cybercrime, the need for skilled cybersecurity experts has never been greater. Professionals who complete the Cyber Security Job Ready Program training in Chandrapur are prepared for a range of roles such as Security Analyst, Ethical Hacker, SOC Analyst, Cybersecurity Consultant, Network Security Engineer, and more. These roles span across sectors including finance, healthcare, government, telecommunications, and e-commerce.
Moreover, cybersecurity professionals are among the highest-paid IT professionals globally. Certifications embedded in this training such as CEH (Certified Ethical Hacker), CompTIA Security+, and CISSP also significantly increase job market competitiveness and salary potential.
Training Methodology and Expert Instructors
The quality of its teachers is one of the main factors influencing students' preference for this program. In the classroom, seasoned cybersecurity experts with years of field experience impart their knowledge. They assist students on interview techniques, resume construction, and career pathways in addition to teaching.
The curriculum is effective and engaging because of its case-based learning, interactive lectures, and ongoing evaluation. To keep students up to date on the most recent developments in cyber threats, the teachers utilise case studies and the most recent threat data. Learners are introduced to real-world strategies that experts employ on a regular basis, such as breaking down a ransomware assault or mimicking a phishing effort.
Certification and Placement Support
At the end of the program, students receive a certification that validates their expertise in cybersecurity practices. Additionally, those pursuing international certifications are guided throughout their preparation journey. The placement cell assists students with resume building, mock interviews, and connecting with companies hiring for cybersecurity roles.
The practical skills developed during the course make learners stand out in interviews. Companies often hire directly from the pool of students completing the Cyber Security Job Ready Program courses in Chandrapur, due to the job readiness and technical competence imparted by the curriculum.
Why Choose SevenMentor?
When it comes to selecting the right training provider, choosing SevenMentor the best training institute for Cyber Security Job Ready Program Training ensures you're investing in quality, credibility, and real-world relevance. SevenMentor has built a reputation across India for delivering high-impact IT training programs that are aligned with industry requirements. Their structured approach, excellent faculty, strong placement support, and commitment to hands-on learning have made them a trusted name in cybersecurity education.
With a legacy of training thousands of professionals and a placement success rate that stands out, SevenMentor ensures that learners from Chandrapur can access the same high-quality cybersecurity training as students from major metropolitan cities.
The Cyber Security Job Ready Program Classes in Chandrapur are not just an educational course—they are a launchpad into one of the most critical, challenging, and rewarding domains in the tech world. With a curriculum that blends theoretical grounding and real-world practice, learners are transformed into cybersecurity professionals capable of defending digital assets and responding to evolving threats.
The Cyber Security Job Ready Program training in Chandrapur offers the ideal roadmap to success. With the guidance of SevenMentor, the best training institute for Cyber Security Job Ready Program Training, your journey into the cybersecurity workforce is not only well-supported but also industry-validated.
Online Cyber Security Job Ready Program Training
SevenMentor offers a comprehensive online Cyber Security Job Ready Program Training in Chandrapur, providing a flexible yet equally robust alternative. Through SevenMentor’s immersive digital platform, students can access live instructor-led sessions, recorded lectures, virtual labs, and real-time doubt-solving.
This format is ideal for working professionals or students who require the flexibility of learning at their own pace. The online program ensures that the same rigor, interactivity, and support are maintained. Learners also have access to online forums, one-on-one mentoring sessions, and mock interviews—all designed to mirror the classroom experience as closely as possible.
Corporate Cyber Security Job Ready Program Course
SevenMentor offers a customized corporate Cyber Security Job Ready Program Course in Chandrapur for companies looking to upskill their IT teams, improve their internal security posture, or develop a proactive incident response framework.
Delivered either on-site or virtually, these sessions are designed based on the specific risk profile and operational environment of the organization. Whether it’s training developers on secure coding or helping the IT team establish a Security Operations Center (SOC), the corporate programs are highly practical and goal-oriented.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)