About Cyber Security
In today’s digitally interconnected world, the threat landscape continues to evolve at an unprecedented rate. With the rise in cybercrimes, data breaches, and sophisticated cyber-attacks, there is a growing demand for professionals who can protect information systems and digital infrastructure. The Cyber Security Job Ready Program Classes in Ahmednagar are structured to address these demands with a comprehensive and practical approach to cyber defense strategies. This program is designed for individuals aiming to build a career in the cybersecurity domain by equipping them with industry-relevant skills, real-world projects, and the theoretical foundation needed to thrive in today’s IT security environment.
Understanding the Relevance of Cyber Security Today
Large enterprises and governmental organisations are no longer the only ones concerned about cybersecurity. In actuality, cyber dangers could affect individuals as well as small enterprises, healthcare systems, and educational organisations. The pervasiveness of digital technologies in contemporary life has made people more susceptible to cyberattacks. Because of this, cybersecurity is now a crucial function in many different industries.
Professionals trained in cybersecurity are in high demand, not just to protect organizational data but to ensure business continuity, comply with regulatory frameworks, and maintain customer trust. The Cyber Security Job Ready Program courses in Ahmednagar are designed to prepare individuals to meet these challenges head-on, covering the full spectrum of cybersecurity concepts including threat analysis, network security, risk management, cryptography, and ethical hacking.
Why Choose a Cyber Security Job Ready Program?
A Cyber Security Job Ready Program stands out because it bridges the gap between academic knowledge and practical, job-ready skills. Unlike traditional education models that focus heavily on theoretical concepts, this program emphasizes practical application, real-time threat detection, and remediation techniques. Participants learn how to secure networks, respond to security incidents, and implement security policies that align with global standards and best practices.
Through a structured curriculum, learners gain hands-on experience using industry tools, simulated environments, and live case studies that mimic real-world scenarios. By the end of the program, students are not only knowledgeable about cybersecurity principles but are also capable of applying them in various IT ecosystems.
Scope and Career Opportunities in Cyber Security
Cybersecurity offers an extensive range of career opportunities across multiple domains such as banking, finance, healthcare, education, and IT services. Job roles include Security Analyst, Penetration Tester, Security Consultant, Network Security Engineer, and Security Architect, among others. With more companies moving to digital platforms, cloud services, and remote work models, the demand for skilled cybersecurity professionals has surged significantly.
The Cyber Security Job Ready Program training in Ahmednagar ensures that learners are well-prepared to take on these roles with confidence. The training includes certifications and project-based assessments that enhance the employability of graduates, making them suitable candidates for competitive positions in the cybersecurity job market.
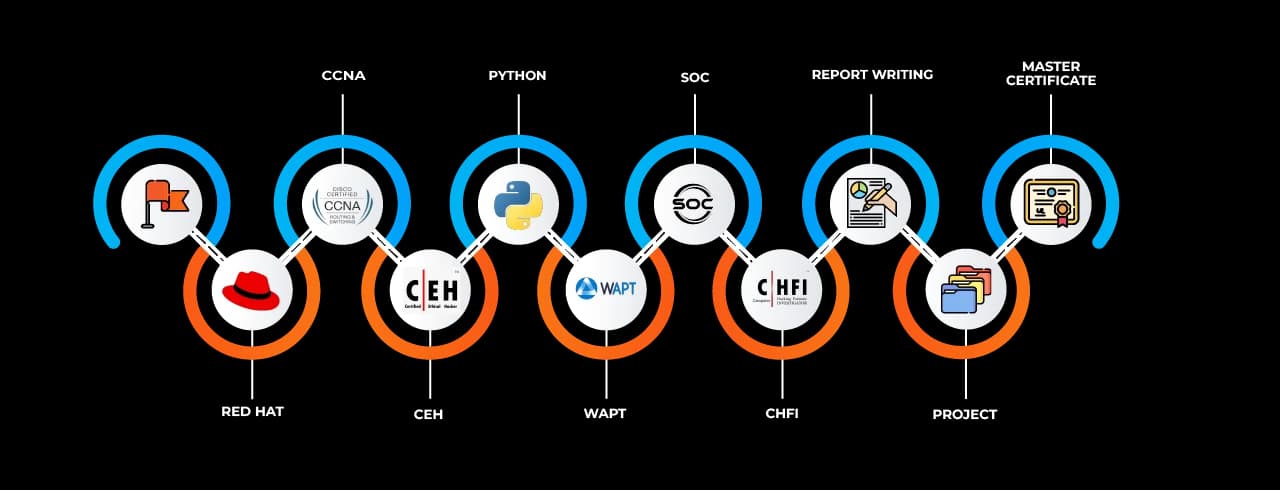
Training Curriculum Overview
The Cyber Security Job Ready Program follows a dynamic and evolving curriculum aligned with current industry needs. It starts with an introduction to the basics of cybersecurity, such as information security fundamentals, cyber threat landscape, and security protocols. From there, students move on to intermediate and advanced topics including network security, intrusion detection systems, malware analysis, vulnerability assessment, incident response, and digital forensics.
Specialized modules cover ethical hacking, security information and event management (SIEM), firewalls, and encryption techniques. The program also emphasizes compliance with international standards such as ISO 27001, NIST, and GDPR. Additionally, learners receive training in popular tools and platforms like Wireshark, Kali Linux, Metasploit, and Nessus, providing practical exposure to cybersecurity operations.
Hands-On Learning and Real-Time Projects
One of the defining features of the Cyber Security Job Ready Program Classes in Ahmednagar is its hands-on approach to learning. Participants engage in live labs, penetration testing simulations, and red vs blue team exercises that simulate cyber attack and defense strategies. These real-time projects are designed to build critical thinking, analytical skills, and technical expertise.
The curriculum includes multiple case studies from different industries to help learners understand how cybersecurity is implemented in diverse environments. Whether it is safeguarding a financial system from phishing attacks or protecting a healthcare database from ransomware, the scenarios mirror current real-world security challenges.
Expert Mentors and Industry Trainers
The strength of any training program lies in its instructors. The Cyber Security Job Ready Program training in Ahmednagar offered by SevenMentor is led by certified cybersecurity experts and seasoned professionals who bring decades of industry experience to the classroom. These mentors have worked with multinational companies, government agencies, and cybersecurity firms, and they share their insights, experiences, and best practices with students throughout the program.
Regular workshops, guest lectures, and interactive Q&A sessions ensure that learners stay updated with the latest threats, trends, and technologies in cybersecurity. With personalized mentorship, learners are guided in their career planning, interview preparation, and certification exams, adding significant value to the training experience.
Placement Assistance and Certification
Completing the Cyber Security Job Ready Program courses in Ahmednagar comes with the added advantage of placement support and globally recognized certifications. The program includes resume-building sessions, mock interviews, and aptitude training to prepare candidates for the job market. Industry connections, tie-ups with hiring partners, and dedicated career services help students secure positions in reputed companies.
Participants receive certificates that validate their skills and enhance their professional credibility. These certifications act as a gateway to higher-level cybersecurity roles and provide a competitive edge in job interviews and performance evaluations.
Infrastructure and Learning Environment
SevenMentor, the best training institute for Cyber Security Job Ready Program Training, provides a state-of-the-art learning environment in Ahmednagar. The institute features modern classrooms, dedicated labs, and access to cutting-edge software tools. High-speed internet, virtual machines for cybersecurity experiments, and a rich library of digital resources further enrich the learning experience.
The institute also fosters a collaborative atmosphere where students can work on group projects, participate in hackathons, and attend cybersecurity meetups. This interactive and engaging setting encourages continuous learning and helps build a strong professional network within the cybersecurity community.
Flexible Learning Schedules
Understanding the diverse backgrounds of learners, SevenMentor offers flexible schedules for the Cyber Security Job Ready Program. Whether you're a full-time student, a working professional, or someone returning to the workforce, the program provides weekday and weekend batches, as well as evening classes.
Additionally, learners have access to recorded sessions, online resources, and live doubt-clearing sessions, ensuring that they can keep up with the curriculum at their own pace. This adaptability makes the Cyber Security Job Ready Program training in Ahmednagar accessible and convenient without compromising on quality.
The Cyber Security Job Ready Program Classes in Ahmednagar offer a practical and immersive approach to building a career in cybersecurity. With a strong focus on hands-on experience, real-world applications, and mentorship from industry veterans, the program prepares learners to meet the challenges of a complex cybersecurity landscape. From securing network infrastructures to preventing sophisticated attacks, students are empowered with the skills and confidence required to become successful cybersecurity professionals.
Online Classes
SevenMentor offers an excellent online Cyber Security Job Ready Program training of the. The online training delivers the same high-quality curriculum through interactive live sessions, recorded lectures, and virtual labs. Students can participate in real-time discussions, complete assignments digitally, and work on virtual cybersecurity projects from anywhere in the world.
This mode of training is ideal for working professionals, remote learners, or those with scheduling constraints. Despite being remote, the online classes maintain the same standard of practical exposure and engagement as in-person classes, with constant mentor support and regular assessments. Learners also get access to a dedicated learning management system (LMS) where they can track their progress, download study materials, and submit projects.
Corporate Training
SevenMentor offers corporate Cyber Security Job Ready Program training solutions. The corporate version of the Cyber Security Job Ready Program is tailored to the specific needs of companies, focusing on the existing skill gaps, security requirements, and technology stack used by the organization.
Delivered either onsite or virtually, the training modules are highly customizable and are designed in consultation with the client to ensure relevance and effectiveness. Topics can include internal threat management, secure application development, compliance audits, and incident response strategies.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)