About Cyber Security
As the digital landscape rapidly evolves, the threats to data and IT infrastructure are growing more sophisticated than ever. Organizations across the globe are investing heavily in cybersecurity measures to protect their assets, creating a huge demand for qualified professionals in this field. This has made cybersecurity one of the most critical and rewarding domains in the IT industry today. To cater to this demand, Cyber Security Job Ready Program Classes in Kolhapur offer a comprehensive approach to cybersecurity education, equipping students with both theoretical knowledge and hands-on skills.
This specialised training program covers the newest tools, defensive tactics, incident response plans, and real-world threats to prepare applicants for the workforce right away. This course gives you the knowledge and experience you need to succeed in the cybersecurity field, regardless of whether you're a recent graduate or an IT professional looking to change your career path. This curriculum in Kolhapur guarantees that students are knowledgeable about the basic and advanced concepts of cybersecurity, network security, ethical hacking, and more. It is taught by professionals in the field and is in line with current trends.
Program Overview
The Cyber Security Job Ready Program training in Kolhapur is curated to meet industry requirements by focusing on practical application rather than mere theoretical concepts. The course structure begins with the foundational principles of cybersecurity, such as confidentiality, integrity, availability, and risk management. As learners progress, they delve into specialized areas like security architecture, identity and access management, cryptography, penetration testing, SIEM (Security Information and Event Management), threat intelligence, and cloud security.
Students are provided access to simulated lab environments where they can experiment with real-world tools used by cybersecurity professionals. Tools like Wireshark, Metasploit, Burp Suite, Nmap, Nessus, and Splunk are extensively used throughout the training. This hands-on exposure not only builds technical confidence but also gives learners an edge when facing technical interviews or real-time job responsibilities.
Learning Objectives
The core objective of the Cyber Security Job Ready Program courses in Kolhapur is to enable learners to develop a robust security mindset and to understand the methodologies used to detect, analyze, and mitigate cyber threats. It also aims to build competence in ethical hacking practices, vulnerability assessment, incident detection and response, firewall configuration, and security compliance.
In order to properly construct defensive measures, the training places a strong emphasis on a scenario-based learning style that teaches participants to think like attackers. In addition, students receive extensive instruction in scripting, operating systems (Windows and Linux), and programming languages like Python and PowerShell, which are vital for threat analysis and automation.
Industry-Relevant Curriculum
One of the major strengths of the SevenMentor Cyber Security Job Ready Program Classes in Kolhapur is the highly dynamic and updated curriculum, which evolves according to the changing threat landscape and technological advancements. The course includes modules on: Cybersecurity principles and governance, Network protocols and security controls, Web application security and OWASP Top 10, Digital forensics and malware analysis, Intrusion detection and prevention systems, Advanced persistent threats (APTs) and zero-day vulnerabilities, Security policies, audits, and compliance frameworks like ISO/IEC 27001, PCI-DSS, and GDPR.
Every topic is covered with in-depth technical analysis and is accompanied by use-cases that reflect actual cybersecurity breaches and how they were mitigated.
Career Outcomes and Certification
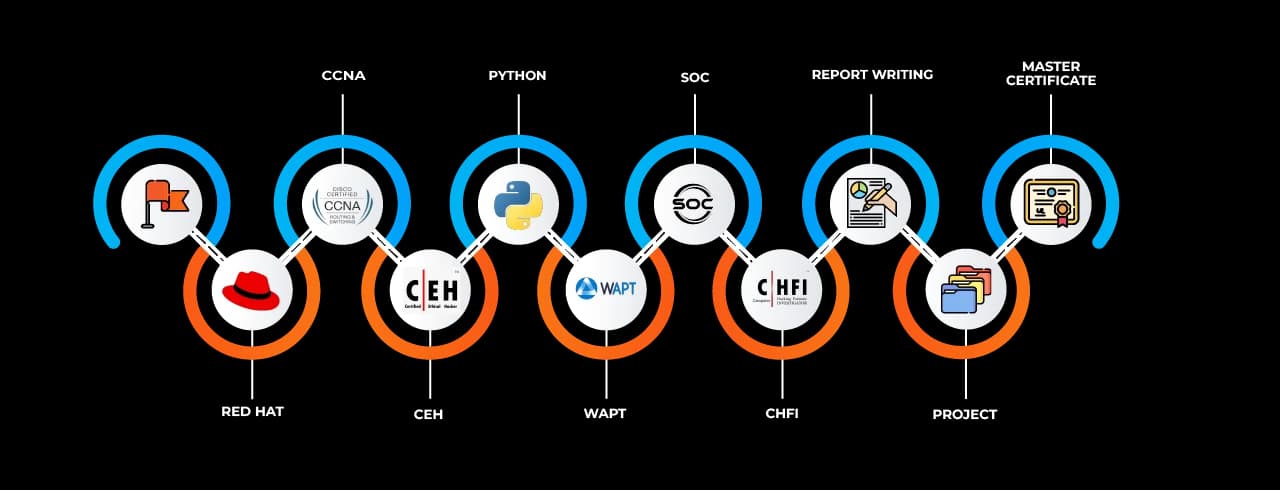
Completing the Cyber Security Job Ready Program training in Kolhapur at SevenMentor opens up multiple career opportunities such as Security Analyst, Penetration Tester, Cybersecurity Consultant, SOC Analyst, Incident Responder, and Ethical Hacker. Learners are also guided toward achieving internationally recognized certifications like CompTIA Security+, CEH (Certified Ethical Hacker), CISSP (Certified Information Systems Security Professional), and OSCP (Offensive Security Certified Professional).
The training not only prepares students for these certifications but also ensures that they have hands-on experience with the practical aspects of each domain. This dual focus on certification and skill-building increases employability and professional credibility in the global job market.
About SevenMentor
SevenMentor, the best training institute for Cyber Security Job Ready Program Training stands out for its student-centric approach and commitment to quality education. The institute offers a learning environment that combines academic rigor with practical implementation, ensuring that students receive a holistic understanding of cybersecurity concepts.
At SevenMentor, the faculty comprises cybersecurity experts with years of experience in handling critical information security projects for Fortune 500 companies. This real-world experience translates into valuable insights for learners, helping them grasp complex topics more easily and apply them effectively.
Another key advantage of SevenMentor is its emphasis on mentorship. Each student is guided individually by trainers who monitor their progress and help them overcome learning challenges. This mentorship model has proven highly effective in improving retention, performance, and job readiness.
Infrastructure and Learning Support
The training environment at SevenMentor is equipped with advanced labs that simulate enterprise-level security networks, enabling learners to practice defending systems in a controlled setup. Every learner gets access to cloud-based lab environments, source code repositories, and security toolkits to support hands-on learning.
In addition to the classroom sessions, students are also provided with self-paced modules, recorded sessions, interactive assignments, and quizzes to reinforce their understanding. Weekly tests and real-time assessments are conducted to ensure consistent progress and identify areas that require additional focus.
Placement Assistance and Industry Exposure
One of the significant advantages of enrolling in the Cyber Security Job Ready Program Classes in Kolhapur at SevenMentor is the comprehensive placement support. The institute has established connections with multiple tech firms and security solution providers that frequently hire directly from the training batches.
Students benefit from resume-building workshops, mock interviews, aptitude training, and career counseling sessions designed to prepare them for the competitive job market. Alumni of this program have successfully secured positions in reputed organizations across India and abroad, a testament to the institute’s training quality and placement support.
Moreover, regular webinars, hackathons, and guest lectures by industry experts keep learners informed about the latest trends and challenges in the cybersecurity landscape. This exposure not only expands their knowledge but also enhances their professional network.
In today’s interconnected world, cybersecurity professionals are indispensable. The threat of cyber attacks looms large over businesses, governments, and individuals alike, making it crucial to have skilled defenders at every level. The Cyber Security Job Ready Program courses in Kolhapur are designed to bridge the gap between academic learning and practical application, making students job-ready and industry-relevant from the very first day of their career.
Online Classes
SevenMentor offers an equally effective online Cyber Security Job Ready Program training in Kolhapur. The online training is structured to match the quality and depth of classroom sessions, with live instructor-led classes, cloud-based lab access, and 24/7 support.
Learners can attend sessions from the comfort of their homes and still interact with instructors in real time. Recorded lectures are available for revision, and all resources including assignments, lab exercises, and discussion forums are provided via an integrated learning management system. This flexibility makes the course accessible without compromising on quality, making it ideal for working professionals and students alike.
Corporate Training
SevenMentor offers customized corporate Cyber Security Job Ready Program training. The customized corporate modules under the Cyber Security Job Ready Program courses in Kolhapur are tailored to suit specific business requirements, industry compliance standards, and employee roles.
These corporate training sessions are delivered on-site or online, based on the organization’s preference, and include real-world case studies, threat simulations, and role-based learning. SevenMentor’s trainers work closely with the enterprise IT teams to ensure the training aligns with their cybersecurity framework and policies. With a focus on measurable outcomes, SevenMentor’s corporate cybersecurity training delivers both technical value and strategic benefit.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)