About Cyber Security
In the ever-evolving landscape of digital threats and technological innovation, cybersecurity has become a non-negotiable priority for organizations across the globe. With the rapid digitization of business processes and the increasing complexity of cyberattacks, skilled cybersecurity professionals are in high demand. Addressing this need, the Cyber Security Job Ready Program Classes in Nanded are tailored to equip aspiring IT professionals with the necessary skills and expertise to thrive in the cybersecurity domain.
This extensive training program aims to produce cybersecurity professionals who are ready for the workforce and is now located in Nanded, a developing centre for education and IT training in Maharashtra. This program provides the technical depth, real-world experience, and industry-aligned curriculum necessary to guarantee career preparation, regardless of whether you're a recent graduate looking to pursue a career in IT or an experienced professional hoping to move into cybersecurity.
Industry Relevance of Cybersecurity Skills
The digital transformation of enterprises, the explosion of data, and the rise in interconnected systems have dramatically increased the attack surface for malicious actors. Cyber threats are not only becoming more frequent but also more sophisticated. To safeguard networks, data, applications, and end-users, organizations need professionals who can anticipate, identify, mitigate, and respond to cyber incidents effectively.
The Cyber Security Job Ready Program training in Nanded is strategically designed to meet these critical industry demands by covering a broad range of topics including threat intelligence, ethical hacking, penetration testing, risk analysis, and incident response.
The course not only imparts theoretical knowledge but also emphasizes application-based learning to develop skills that employers actively seek.
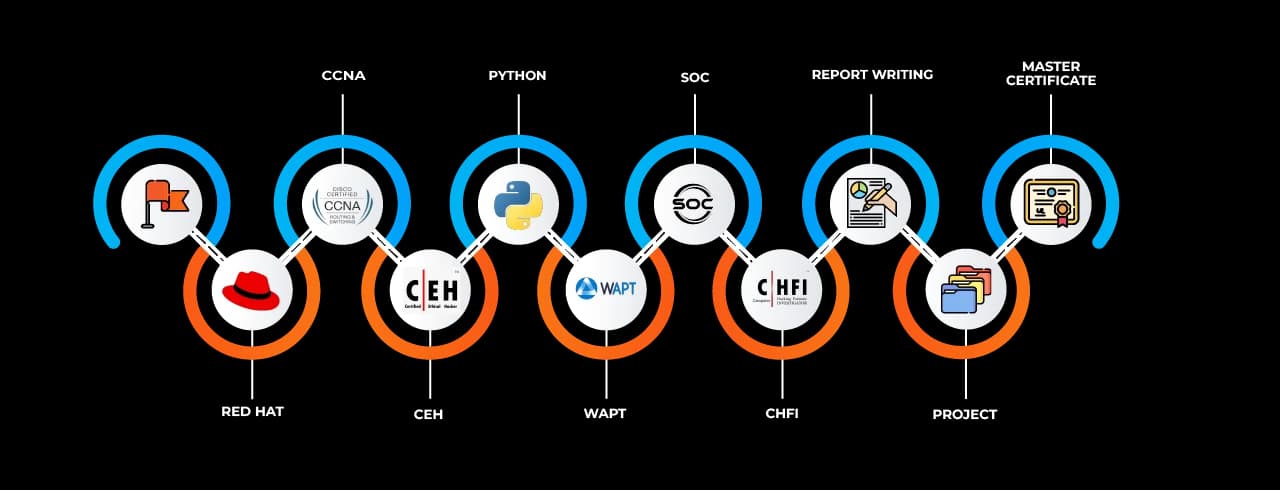
Curriculum Overview
The course at SevenMentor begins by laying a strong foundation in the core concepts of cybersecurity, including understanding security protocols, system architecture, and network infrastructures. As students progress, they dive into topics such as malware analysis, security operations center (SOC) management, vulnerability assessment, and compliance frameworks like ISO/IEC 27001, NIST, and GDPR.
Each module of the Cyber Security Job Ready Program courses in Nanded is carefully curated to align with global industry standards and the evolving threat landscape. The curriculum is updated regularly to reflect the latest developments in cyberattack techniques and defense strategies. Learners are exposed to tools such as Wireshark, Metasploit, Kali Linux, Nessus, and Splunk to understand both offensive and defensive aspects of cybersecurity.
Training Methodology and Learning Approach
The training program emphasizes experiential learning, where students engage in simulations of real-world cyberattacks and security breaches. These scenarios help in developing a problem-solving mindset and the ability to respond quickly under pressure, which are crucial traits in the cybersecurity field.
Participants in the Cyber Security Job Ready Program Classes in Nanded benefit from instructor-led sessions, guided lab practices, and mentor-supported projects. The interactive nature of the program fosters critical thinking, collaboration, and the development of practical skills that translate seamlessly to the workplace.
Another unique aspect of the training is its project-based structure. Capstone projects, red team-blue team exercises, and real-time security audits provide learners with tangible outcomes and experiences they can showcase in job interviews or professional portfolios.
Certification and Placement Assistance
At the end of the training, students receive a certification that validates their competency in cybersecurity principles and practices. The credential serves as a testament to their readiness for job roles such as Security Analyst, SOC Engineer, Penetration Tester, Cybersecurity Consultant, and Incident Responder.
Furthermore, the Cyber Security Job Ready Program training in Nanded offered by SevenMentor is supplemented with placement assistance services. Resume building workshops, mock interviews, aptitude preparation, and employer connections are part of the comprehensive support system designed to help students transition smoothly into the job market.
The placement cell at SevenMentor maintains strong ties with cybersecurity firms, IT companies, and enterprise organizations, thereby providing learners with direct access to job opportunities.
Why Choose SevenMentor?
SevenMentor, the best training institute for Cyber Security Job Ready Program Training, stands out for its commitment to excellence, industry alignment, and student success. The institute has built a reputation for delivering high-quality, results-oriented IT training programs.
SevenMentor’s faculty includes seasoned cybersecurity professionals with extensive experience in threat hunting, incident response, and secure infrastructure management. Their industry insights and practical exposure enrich the learning environment, making the content both relevant and impactful.
In addition to its state-of-the-art infrastructure and real-time lab environments, SevenMentor also offers flexible batch timings, weekend classes, and one-on-one mentoring, ensuring that learners from diverse backgrounds can benefit from the program.
Career Opportunities After the Program
The successful completion of the Cyber Security Job Ready Program Courses in Nanded opens the door to a variety of career paths. With cybersecurity being a high-demand domain, job opportunities are abundant not only in IT companies but also across finance, healthcare, telecom, manufacturing, and government sectors.
Candidates trained through this program are well-equipped to handle job roles such as Security Analyst, Information Security Officer, SOC Specialist, Application Security Engineer, and even roles in compliance and risk management. The growing integration of AI and cloud technologies with cybersecurity also provides avenues for future specialization in domains such as cloud security and machine learning for threat detection.
Employers today look for job-ready professionals who can contribute from day one, and that’s precisely the goal of the Cyber Security Job Ready Program training in Nanded, to produce professionals who are not just knowledgeable but also deployment-ready.
Program Flexibility and Batch Schedules
Recognizing the diverse backgrounds and commitments of its learners, the program offers flexible learning options. Students can choose from weekday, weekend, or fast-track batches, making it easier for working professionals and college students to enroll without disrupting their current schedules.
SevenMentor also supports hybrid learning environments where physical classroom sessions can be combined with online lab access, ensuring that students can practice skills at their own pace while staying aligned with the instructor-led curriculum.
As the cybersecurity landscape continues to grow in complexity, the need for skilled professionals who can defend against advanced threats is more urgent than ever. The Cyber Security Job Ready Program Classes in Nanded serve as a robust launchpad for individuals looking to build or advance their careers in this high-growth domain. With its industry-focused curriculum, hands-on labs, expert mentorship, and placement support, the program delivers a comprehensive pathway to a successful cybersecurity career.
Online Classes
SevenMentor offers robust online Cyber Security Job Ready Program training. The online Cyber Security Job Ready Program training in Nanded retains all the features of the in-class program — live instructor-led sessions, practical lab exercises, real-time projects, and mentorship. Learners get access to a virtual lab setup that mirrors a real-world enterprise IT environment, allowing them to gain hands-on experience with security tools and techniques from the comfort of their home.
The online training platform also includes discussion forums, recorded sessions for revision, and periodic assessments to track progress. SevenMentor’s online training maintains high interactivity and student engagement, with regular Q&A sessions, doubt-clearing classes, and project feedback, ensuring that distance never becomes a barrier to quality education.
Corporate Training
SevenMentor offers tailored corporate Cyber Security Job Ready Program training solutions for companies looking to upskill their IT teams. With the rise in cyber incidents affecting businesses across all sectors, employee awareness and technical proficiency in cybersecurity are critical. SevenMentor collaborates with organizations in Nanded and beyond to deliver customized cybersecurity training programs that address specific enterprise needs. Sessions can be conducted onsite or virtually, depending on organizational preferences, and are led by industry-certified instructors with corporate training experience.
The Cyber Security Job Ready Program training in Nanded offered for corporates includes assessments, reporting, and post-training support to ensure knowledge retention and practical application. This service helps businesses strengthen their internal security posture while also contributing to employee satisfaction and career growth.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)