About Cyber Security
In the digital age, where cyber threats evolve faster than ever, cyber security has become a critical pillar for individuals, businesses, and government institutions. The demand for skilled professionals who can safeguard data, infrastructure, and digital identities is skyrocketing, making cyber security a dynamic and rewarding career path. Cyber Security Job Ready Program Classes in Nagpur have been specifically designed to bridge the skill gap and equip students and professionals with hands-on expertise, real-time defense strategies, and industry-accepted knowledge.
Nagpur, an emerging IT hub in Central India, has become an educational and technological hotspot. The city has seen a significant rise in learners actively pursuing niche and high-demand fields such as cyber security. The Cyber Security Job Ready Program training in Nagpur is gaining popularity because of its practical orientation, relevance to the latest technological developments, and its alignment with global security standards. This program focuses not only on theoretical concepts but also on real-world simulations and hands-on labs, ensuring that learners are not only aware of threats but also capable of effectively responding to them.
Program Overview and Curriculum Focus
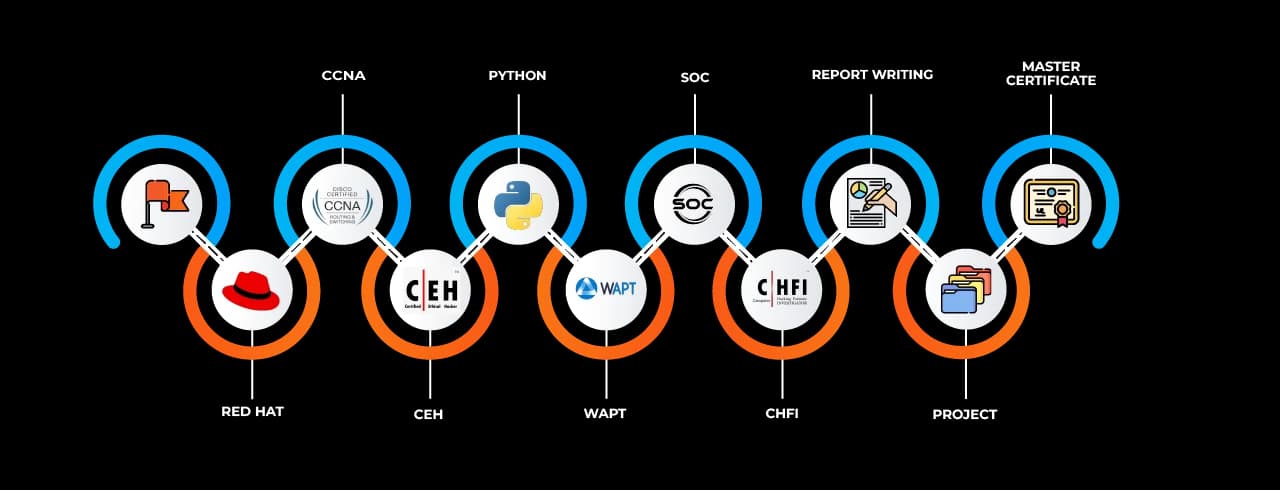
The Cyber Security Job Ready Program courses in Nagpur at SevenMentor cover an expansive syllabus that is in line with international frameworks and compliance guidelines. The curriculum includes a foundational understanding of cyber security concepts, the principles of network and application security, ethical hacking methodologies, penetration testing, malware analysis, cryptography, secure coding practices, cloud security, and incident response planning.
Additionally, the training incorporates governance, risk management, and compliance (GRC) modules, which allow students to evaluate an organization's overall security posture. The course guarantees that students acquire a comprehensive understanding of cyber risk mitigation by covering both offensive and defensive cyber security approaches.
This course stands out for its practical focus; real-life attack and defence scenarios are simulated through hands-on labs, red teaming/blue teaming exercises, and access to real-time threat intelligence platforms. Students are taught how to conduct vulnerability assessments and security audits using a variety of security tools, including Wireshark, Metasploit, Burp Suite, Nessus, Nmap, and many more.
Target Audience and Career Opportunities
This program is structured to cater to a broad range of audiences. Fresh graduates from IT, computer science, electronics, or other STEM disciplines who are interested in entering the cyber security domain will find this course to be a strong foundation for launching their careers. Similarly, working professionals from IT support, network administration, or software development backgrounds can pivot into the cyber security field through this upskilling program.
After completing the Cyber Security Job Ready Program training in Nagpur, learners become eligible for roles such as Security Analyst, Ethical Hacker, Penetration Tester, SOC Analyst, Security Consultant, Incident Responder, and Information Security Officer. Moreover, the course acts as a preparatory platform for globally recognized certifications such as CEH, CompTIA Security+, OSCP, and CISSP.
About SevenMentor
SevenMentor, the best training institute for Cyber Security Job Ready Program Training has built a reputation for delivering consistent, high-quality education. Known for its strong industry connections and real-time project experience, SevenMentor offers students and professionals a chance to learn directly from certified trainers and cyber security experts.
The institute’s well-structured methodology ensures that learners not only grasp conceptual knowledge but also develop the ability to apply that knowledge in real-world settings. Through a combination of mentor-led instruction, lab-intensive sessions, and detailed assessments, SevenMentor guarantees both comprehension and competency.
What sets SevenMentor apart is its mentorship model and dedicated placement assistance. After completion of the program, learners receive continuous guidance on building professional resumes, facing technical interviews, and applying to relevant job roles across the country. With its extensive placement network, students are placed in top companies that require qualified and capable cyber security professionals.
Learning Infrastructure and Facilities
The Cyber Security Job Ready Program Classes in Nagpur offered by SevenMentor are delivered through a combination of interactive classroom sessions and practical lab work. The Nagpur training center is equipped with modern facilities including high-speed internet, real-time simulation labs, and collaborative spaces that encourage problem-solving and innovation.
Each student is provided with dedicated access to virtual machines and pre-configured environments for safely executing cyber security tests and research. The labs are sandboxed, enabling learners to experiment with exploits, perform intrusion detection, analyze malware, and practice forensics without the risk of harming live systems.
In addition, SevenMentor provides access to a cloud-based learning management system (LMS) which hosts recorded lectures, practice assignments, additional reading material, and quiz-based assessments. This allows students to revisit content, revise modules at their own pace, and track their learning progress.
Industry Relevance and Placement Assistance
The ever-increasing volume and sophistication of cyber threats have made it essential for organizations to maintain an internal team of cyber security professionals who can anticipate, detect, and respond to attacks. Hence, job-ready programs must prepare learners for this reality. The Cyber Security Job Ready Program courses in Nagpur have been crafted with the latest hiring trends, job descriptions, and skill requirements in mind.
Candidates with practical experience, problem-solving talents, and familiarity with contemporary security tools and platforms are highly valued by recruiters nowadays. Recognising this need, SevenMentor uses capture-the-flag contests, hackathon challenges, practice interviews, and useful evaluation frameworks to get candidates ready. Real-world situations like ransomware attacks, DDoS defence tactics, and audits of cloud misconfiguration are presented to students.
This practical orientation significantly boosts learner employability, ensuring they are prepared to meet job market expectations from the very first day of employment. The placement support team at SevenMentor works closely with learners to match them with the right job profiles, schedule interviews, and connect them with hiring partners across India’s tech landscape.
Certification and Professional Development
Upon successful completion of the Cyber Security Job Ready Program Classes in Nagpur, learners receive a certification of completion from SevenMentor. This certificate is a mark of credibility and is recognized by employers as evidence of advanced cyber security training. Additionally, the course syllabus aligns with the core domains of global certifications, allowing learners to further enhance their profile by appearing for exams like CEH, CompTIA Security+, or even OSCP for advanced learners.
To support continuous professional development, SevenMentor offers alumni access to knowledge-sharing sessions, security webinars, and live threat intelligence briefings. These sessions keep learners updated with evolving threat landscapes, policy regulations like GDPR and HIPAA, and advancements in security technology.
The rise in digital transformation, cloud adoption, remote work, and interconnected devices has made cyber security one of the most critical areas in today’s IT ecosystem. As attacks become more targeted and sophisticated, the need for professionals trained in cyber defense, ethical hacking, and risk mitigation continues to grow. The Cyber Security Job Ready Program training in Nagpur offers a thorough and practical approach to cyber security education, ensuring learners are not only knowledgeable but also job-ready from day one.
Online Classes
SevenMentor offers a comprehensive online Cyber Security Job Ready Program Classes in Nagpur. This online format retains the same rigorous curriculum, practical labs, and live mentorship, but adds the convenience of remote access. Through interactive live sessions, learners can engage with instructors in real-time, clear their doubts, and collaborate with peers through virtual breakout rooms.
The online platform includes a full-featured virtual lab environment where students can perform hands-on tasks such as vulnerability scanning, traffic analysis, brute-force simulations, and more. These labs are browser-accessible and do not require high-end personal systems, making them ideal for learners across varied infrastructure capabilities. Quizzes, live assessments, and regular feedback sessions ensure learners stay on track. The online course also includes access to recorded lectures for revision and self-paced learning.
Corporate Training
SevenMentor offers tailored corporate Cyber Security Job Ready Program training in Nagpur to corporate clients aiming to upskill their workforce. These corporate training programs are designed in consultation with business leaders and IT security heads to align with organizational objectives. Training can be delivered on-premises or virtually and focuses on customized content such as compliance requirements, industry-specific threat models, and internal policy alignment. Whether it’s secure application development, advanced incident response, or threat hunting, the corporate curriculum is adapted for specific organizational roles and functions.
Participants in the corporate program benefit from team-based exercises, simulation-based learning, and post-training evaluations. Detailed reports help organizations assess skill gaps, track improvements, and identify further training needs. Additionally, post-training support and refresher sessions ensure that employees stay updated with new threats and regulatory changes.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)