About Cyber Security
In today’s hyper-connected digital ecosystem, cybersecurity has become a fundamental pillar for organizations and individuals alike. With the persistent surge in cyber threats, security breaches, ransomware attacks, and data leaks, there is an acute demand for professionals equipped with cutting-edge cybersecurity skills. The Cyber Security Job Ready Program Classes in Parbhani offer an advanced, industry-aligned curriculum tailored to prepare students for immediate roles in cybersecurity. Whether you are a fresh graduate, a working professional aiming to shift your domain, or an IT enthusiast interested in security, this program provides a concrete foundation and real-world skills to launch your career in the cybersecurity domain.
Designed with a hands-on approach and job-readiness at its core, the program focuses on the most in-demand skills required by employers. It bridges the gap between academic knowledge and practical implementation, ensuring that learners gain the competence needed to tackle evolving cyber challenges across various IT environments.
Industry-Centric Curriculum with Real-Time Implementation
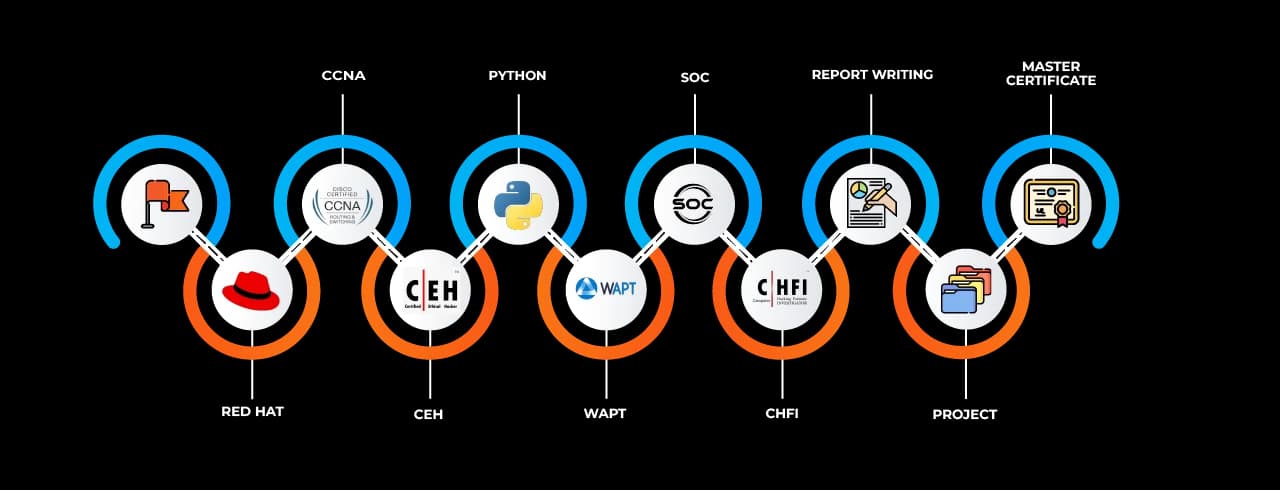
The Cyber Security Job Ready Program training in Parbhani features a comprehensive curriculum mapped to global industry standards. Learners are introduced to core and advanced modules that cover areas such as network security, endpoint protection, ethical hacking, malware analysis, penetration testing, threat intelligence, and vulnerability assessment. Additionally, training modules include Security Information and Event Management (SIEM), cloud security, governance, risk and compliance (GRC), cryptography, and secure software development lifecycle (SDLC).
Students participate in scenario-based learning environments that mimic actual attacks and defences from the very first session. In addition to improving technical depth, this applied learning method fosters the analytical thinking and incident response techniques that are essential for any cybersecurity practitioner. Key certifications like CEH, CompTIA Security+, and CISSP are emphasised as benchmarks, but the course itself is technology-neutral to maximise flexibility.
Labs and virtual environments are an integral part of the program, enabling learners to test tools like Wireshark, Kali Linux, Metasploit, Burp Suite, Nessus, and Snort. These technologies form the backbone of cybersecurity analysis and are extensively used in enterprise-grade security operations centers (SOCs). Moreover, training is infused with the latest developments in Zero Trust security architecture, artificial intelligence in cybersecurity, and next-generation firewalls.
Faculty with Industry Experience and Global Exposure
The quality of instruction is a defining aspect of any technical program. SevenMentor, the best training institute for Cyber Security Job Ready Program Training, ensures that all trainers are not only certified in various security domains but also have rich hands-on experience in managing large-scale cybersecurity operations. The trainers bring in knowledge from across sectors such as finance, healthcare, e-commerce, telecom, and government, providing learners with a broad perspective on the application of cybersecurity in various domains.
The faculty utilizes case studies, breach analysis reports, live projects, and simulated attack-defense drills to prepare students for challenges in the real world. Learners benefit from mentorship, personalized feedback, and interview guidance as part of their training journey, ensuring a holistic and industry-ready experience.
Career Mapping and Job Readiness Focus
A defining feature of the Cyber Security Job Ready Program Courses in Parbhani is the emphasis on job-oriented outcomes. The program goes beyond teaching technical concepts by integrating training for soft skills, resume building, and interview preparation. Career guidance sessions with security leaders and HR professionals offer insights into recruitment patterns, skill benchmarks, and salary trends.
By matching students with businesses that require cybersecurity analysts, penetration testers, SOC engineers, and compliance professionals, SevenMentor's placement support team helps students with job interviews, internships, and referral programs. In addition to providing training, our career-focused design makes sure that students are well-positioned for employment as soon as they finish their courses.
After completing the curriculum, students can work in digital forensics, DevSecOps, cloud security architecture, IT security audits, and red and blue team operations. As more businesses place a higher priority on data security and digital resilience, there is a growing need for cybersecurity specialists in India, particularly in Tier 2 cities like Parbhani. Graduates of this program can play a vital role in assisting companies in safeguarding their digital infrastructure.
Infrastructure and Learning Environment
The physical and digital infrastructure provided by SevenMentor plays a pivotal role in enhancing the learning experience. The institute features advanced labs, high-speed internet, cybersecurity simulation platforms, and virtual machines configured for various attack and defense scenarios. Each classroom is equipped with projection systems and learning management software that supports interactive sessions and immediate practice.
Moreover, students gain access to an exclusive learning portal that includes recorded lectures, reference guides, assessment tools, and doubt-clearing forums. This blended learning environment ensures that students can revise concepts at their own pace and revisit complex topics as needed.
Certifications and Industry Alignment
Certifications are a key part of building credibility in the cybersecurity domain. The Cyber Security Job Ready Program Classes in Parbhani prepare learners for globally recognized certifications, although the training is focused more on skills than on theoretical coverage. Learners are provided support in understanding exam patterns, question formats, and time management strategies for certifications such as Certified Ethical Hacker (CEH), CompTIA Security+, and Certified SOC Analyst (CSA).
Additionally, case studies and assignments are mapped to National Institute of Standards and Technology (NIST), ISO 27001, and OWASP frameworks, providing learners with international context and governance best practices.
Customization and Continuous Learning Support
The cybersecurity field is constantly evolving. New vulnerabilities, emerging threats, and shifting regulatory landscapes mean that cybersecurity training must also evolve. SevenMentor offers lifetime access to updated course material for learners of its Cyber Security Job Ready Program training in Parbhani. Whenever a new technology or attack vector becomes prominent, updated content and additional lab exercises are shared through the learner dashboard.
Furthermore, students can opt for customized specialization modules in areas such as cloud security (AWS/Azure/GCP), IoT security, or blockchain security depending on their interest and career aspirations. These flexible add-on paths allow learners to develop expertise in niche areas that offer greater career growth potential.
As cyber threats grow in frequency and complexity, the demand for trained cybersecurity professionals continues to rise. The Cyber Security Job Ready Program Courses in Parbhani are designed to empower learners with a strong theoretical foundation and significant practical exposure in cybersecurity practices. With advanced labs, experienced instructors, a job-oriented curriculum, and placement assistance, the program ensures complete career preparedness.
Online Classes
SevenMentor offers a fully interactive and flexible online Cyber Security Job Ready Program classes. This online training module replicates the offline classroom experience with live instructor-led sessions, downloadable resources, discussion forums, and real-time query resolution.
Online learners benefit from scheduled virtual labs, simulation-based case studies, and mentor-led project work. The online platform is accessible on both desktop and mobile devices, ensuring uninterrupted learning across geographies. Course recordings are made available for revision and self-paced review, making the program adaptable to busy schedules without compromising on technical rigor or hands-on practice.
Online learners of the Cyber Security Job Ready Program training in Parbhani are also eligible for placement support, certification guidance, and alumni networking. This ensures that the career outcomes are consistent, regardless of the mode of delivery.
Corporate Training
SevenMentor’s corporate training division offers tailored corporate Cyber Security Job Ready Program training. These training sessions can be customized to meet organizational needs—whether it involves internal risk mitigation, external audit readiness, or preparing staff for security certifications.
The corporate training programs align with enterprise goals, include role-based learning paths, and feature post-training assessments to ensure learning retention. Delivered onsite or virtually, these programs address skill gaps and enhance the overall security resilience of the enterprise.
Organizations in Parbhani and surrounding regions can benefit from this corporate partnership by training their employees under the Cyber Security Job Ready Program Courses in Parbhani, delivered by SevenMentor, the best training institute for Cyber Security Job Ready Program Training. This not only enhances internal capabilities but also improves compliance posture and minimizes risk exposure in today’s digital-first business landscape.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)