About Cyber Security
Cybersecurity has become one of the most important areas of the IT business in today's digital-first era. Professionals in cybersecurity play a crucial role in protecting vital infrastructure and safeguarding financial systems. Pursuing specialised cybersecurity education is crucial for Satara's IT enthusiasts and aspiring professionals in order to fulfil the industry's rising expectations. The Cyber Security Job Ready Program Classes in Satara offer a career-defining opportunity to gain comprehensive knowledge and hands-on skills to step confidently into the domain of cyber defense.
The rise in cyber threats, data breaches, and ransomware attacks has made organizations across industries increasingly vigilant about safeguarding their systems and data. As a result, there is a rising demand for professionals who are trained not only in theoretical aspects but are also equipped with real-world expertise to counter evolving cyber threats. The Cyber Security Job Ready Program training in Satara is specifically designed to cater to this requirement, offering an in-depth curriculum focused on making students job-ready.
Overview of the Cyber Security Job Ready Program
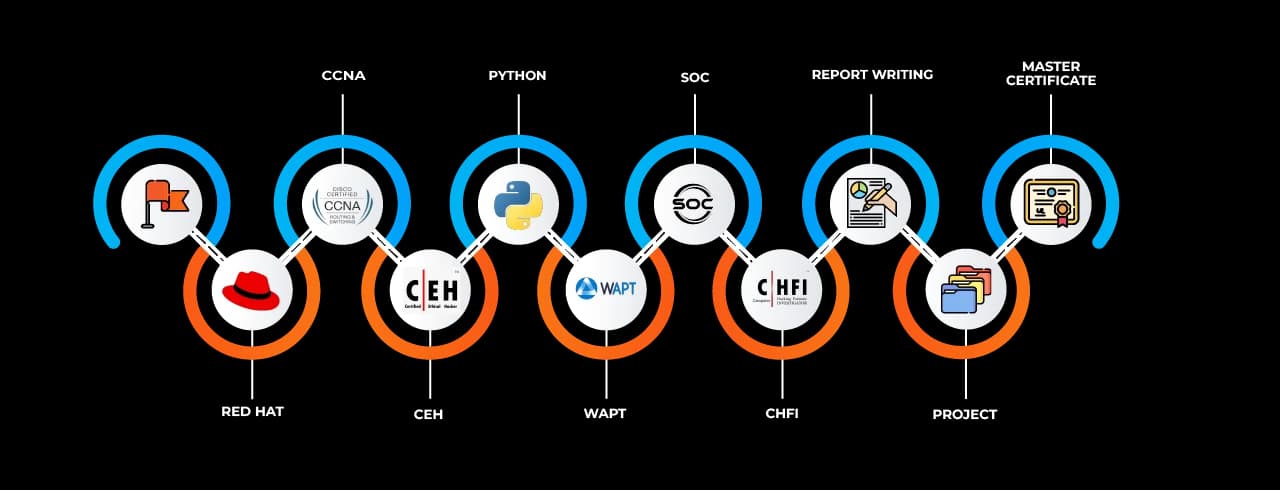
The Cyber Security Job Ready Program courses in Satara are tailored to align with current industry standards and practices. The program covers a wide range of modules including network security, ethical hacking, cryptography, security compliance, endpoint protection, firewalls, intrusion detection systems (IDS), vulnerability assessment, and penetration testing. Each module is curated by industry experts to ensure students learn through real-world use cases, simulated environments, and attack-defense scenarios.
This training does not rely solely on textbooks and lectures but provides a hands-on approach where learners work on actual security tools such as Wireshark, Nmap, Burp Suite, Metasploit, and more. The goal of this job-ready program is to produce skilled professionals who can work as cybersecurity analysts, penetration testers, security engineers, incident responders, and digital forensics investigators.
Curriculum Highlights and Tools
The curriculum adopted by the Cyber Security Job Ready Program Classes in Satara offered by SevenMentor starts with foundational topics such as the basics of information security, types of threats and attacks, and understanding of various protocols and network layers. Once the fundamentals are strong, the training progresses into more advanced topics such as malware analysis, security information and event management (SIEM), threat hunting, application security, and cloud security.
Learners are trained to conduct vulnerability assessments and penetration tests in safe lab environments. The training modules also include incident detection and response, which are critical components for minimizing the impact of any cyber breach.
Real-World Oriented Learning Approach
One of the standout features of the Cyber Security Job Ready Program training in Satara at SevenMentor is its commitment to job-readiness. Unlike conventional courses that focus heavily on theory, this program emphasizes practical skills through live projects and simulation exercises. Students are guided to work on capstone projects that mirror real industry problems.
Throughout the course, learners are exposed to scenarios where they must assess risks, mitigate vulnerabilities, implement security policies, and conduct forensic investigations. These hands-on activities help develop analytical thinking, problem-solving abilities, and technical expertise necessary for high-stakes roles in cybersecurity.
Additionally, mock interviews, aptitude tests, and resume-building sessions are integrated into the training to ensure students are well-prepared for recruitment. This comprehensive grooming enhances employability and makes graduates of the program highly desirable candidates in the job market.
Certifications and Career Opportunities
The Cyber Security Job Ready Program courses in Satara also prepare candidates for leading industry certifications such as CompTIA Security+, CEH (Certified Ethical Hacker), CISSP, and more. These certifications are globally recognized and can significantly improve a candidate’s credibility and career prospects.
After successfully completing the training, students can aim for roles such as Cybersecurity Analyst, Security Operations Center (SOC) Engineer, Penetration Tester, Security Auditor, Risk Assessor, and even move toward leadership roles like Chief Information Security Officer (CISO) over time. The demand for cybersecurity experts is not limited to IT companies; sectors like healthcare, banking, government, and manufacturing also offer lucrative opportunities.
Faculty and Mentorship
Another defining aspect of the Cyber Security Job Ready Program Classes in Satara is the access students get to highly qualified faculty members. Instructors are seasoned professionals with extensive industry experience and certifications in relevant domains. They bring not only academic knowledge but also practical insights from real cyber incidents and threat mitigation strategies they’ve handled in their careers.
This level of mentorship provides students with guidance that goes beyond books. Interactive sessions, open Q&A formats, and case study discussions ensure an enriching learning environment where students can clarify doubts, share ideas, and receive constructive feedback throughout the course duration.
Infrastructure and Lab Support
SevenMentor, the best training institute for Cyber Security Job Ready Program Training, ensures that students have access to state-of-the-art infrastructure and lab environments that simulate real-world enterprise systems. The cyber labs are equipped with advanced configurations where students can practice ethical hacking, test vulnerabilities, and simulate attacks in a secure setting.
These labs play a crucial role in building confidence and competence. Access to virtualized environments and cloud-based platforms allows learners to understand the complexities of securing both on-premise and cloud-native architectures.
Moreover, students receive lifetime access to course material, recorded sessions, and regular updates, which allows them to stay abreast of changes in the cybersecurity landscape even after course completion.
Placement Support and Industry Tie-Ups
A major advantage of enrolling at SevenMentor, the best training institute for Cyber Security Job Ready Program Training, is its robust placement support. With strong ties to companies in banking, finance, IT services, defense, and telecom sectors, the institute connects learners with top recruiters actively seeking cybersecurity talent.
The placement cell organizes job fairs, placement drives, and direct interviews with hiring partners. Resume preparation, technical interview guidance, and soft skills training are also provided as part of the course, ensuring that students are holistically prepared for their job search.
Internship opportunities are also available for top-performing students, offering valuable experience and potential pre-placement offers.
Why Choose SevenMentor for Cybersecurity Training in Satara?
SevenMentor, the best training institute for Cyber Security Job Ready Program Training, has earned its reputation by consistently delivering high-quality, industry-relevant education. With years of experience and a successful track record, the institute is trusted by thousands of learners and corporate clients across India.
Its Satara branch offers the same standard of excellence as its other metropolitan centers. The trainers’ commitment to personalized mentorship, real-world curriculum, lab access, and comprehensive career support makes it the preferred destination for individuals looking to build a future in cybersecurity.
The institute’s success stories of students securing placements at top-tier companies reinforce its value proposition. Whether you're a fresh graduate or an experienced professional transitioning into cybersecurity, SevenMentor’s Cyber Security Job Ready Program delivers the tools and knowledge needed to succeed.
As cyber threats continue to evolve in complexity and scale, the need for skilled cybersecurity professionals is greater than ever. The Cyber Security Job Ready Program Classes in Satara offer a dynamic and practical path for learners to step into this critical domain with confidence and expertise. With a robust curriculum, expert faculty, cutting-edge labs, and industry-aligned projects, the program ensures that students are job-ready by the time they complete their training.
Online Classes
SevenMentor offers flexible online Cyber Security Job Ready Program training. This online variant of the Cyber Security Job Ready Program courses in Satara maintains the same rigor and curriculum as the in-person classes. With live instructor-led sessions, cloud-based lab access, and continuous assessments, online learners enjoy the same benefits as classroom attendees.
The online format is ideal for working professionals, remote learners, or individuals who prefer learning from the comfort of their homes. All sessions are recorded for later access, allowing flexibility without compromising on content delivery. Online learners also receive placement support and mentorship through virtual meetups, mock interviews, and one-on-one guidance.
Corporate Training
SevenMentor also provides customized corporate Cyber Security Job Ready Program training. This version of the Cyber Security Job Ready Program training in Satara is tailored to address the specific needs and security challenges faced by businesses across various sectors.
Corporate training modules are designed after conducting a detailed assessment of the organization’s current security posture and future requirements. Trainers deliver content that is directly applicable to the company’s environment, ensuring immediate on-the-job applicability. The training can be conducted on-site, at SevenMentor’s Satara center, or entirely online, based on the client’s convenience.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)