About Cyber Security
In today’s digitally driven world, cybersecurity has become a fundamental requirement for organizations and individuals alike. With the increasing number of cyber threats, data breaches, and the rapid shift toward cloud-based infrastructure, the demand for skilled cybersecurity professionals is rising exponentially. The Cyber Security Job Ready Program Classes in Solapur have been meticulously designed to equip learners with industry-relevant skills, real-time knowledge, and hands-on experience that align with the current cybersecurity landscape.
Through a thorough, placement-focused program, world-class cybersecurity training is now available in Solapur, a developing centre for education and industry. The curriculum is designed to provide both fundamental and advanced cybersecurity principles, and it is taught by certified specialists with support from contemporary pedagogy. Learners will be exposed to real-world scenarios and techniques that prepare them for a dynamic career in cybersecurity, ranging from network security to ethical hacking, and from risk assessment to incident response.
The Cyber Security Job Ready Program training in Solapur bridges the gap between academic knowledge and real-time IT security challenges. By simulating real-world cyberattacks and analyzing defense mechanisms, learners gain practical proficiency in dealing with modern cybersecurity threats. The curriculum is aligned with global standards such as NIST, ISO/IEC 27001, and OWASP, ensuring a solid foundation for international employment and certifications.
Course Structure and Curriculum Overview
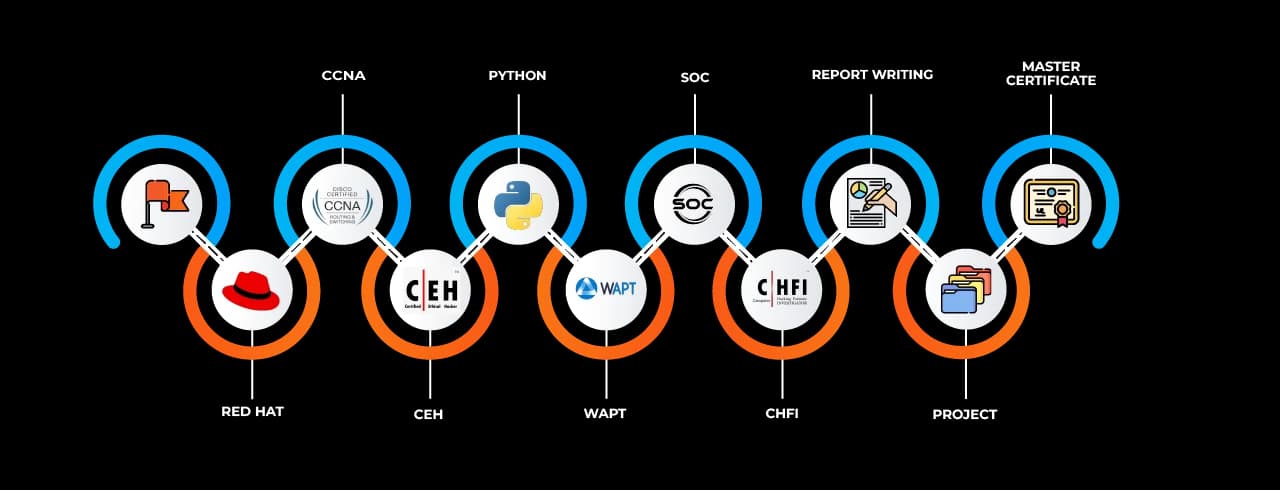
The Cyber Security Job Ready Program Courses in Solapur offered by SevenMentor feature an extensive and evolving curriculum that reflects the demands of the global IT security industry. The training spans across multiple critical areas including: Fundamentals of Information Security and Cyber Laws, Security Architecture and Systems Hardening, Network Security and Secure Communication Protocols, Ethical Hacking and Penetration Testing, SIEM (Security Information and Event Management) Tools, Threat Intelligence and Malware Analysis, Cloud Security and DevSecOps, Incident Response and Forensics.
Learners also engage in case studies, simulations, and project-based learning to ensure a deep, practical understanding. The emphasis on real-time lab environments and cybersecurity toolkits such as Wireshark, Metasploit, Kali Linux, and Splunk ensures that the knowledge gained is immediately applicable in the field.
Each topic is taught with industry-mapped use cases, preparing learners for the actual job roles in domains like threat analysis, vulnerability assessment, cyber forensics, red teaming, and blue teaming. The curriculum is periodically updated in consultation with cybersecurity professionals, ensuring relevance and quality.
Training Methodology
The Cyber Security Job Ready Program Classes in Solapur at SevenMentor follow a progressive learning methodology that combines instructor-led training, hands-on labs, assessments, and mentor feedback. The teaching approach emphasizes critical thinking and problem-solving skills, fostering a mindset required to tackle real-life cyber threats.
All trainers associated with the program are seasoned cybersecurity professionals with certifications such as CEH, CISSP, CompTIA Security+, and OSCP. Their experience in handling enterprise-level cybersecurity challenges adds a unique dimension to the training process, making it not just academic but highly practical.
The program also includes periodic assessments, mock interviews, and aptitude training to make learners truly job-ready. A simulated security operations center (SOC) environment is provided for practical exposure. The inclusion of capstone projects and live threat hunting exercises adds an edge to the learner’s portfolio.
Industry Use Cases and Project-Based Learning
A key aspect of this training is its focus on application-based learning. Learners will be required to analyze recent cyberattack case studies, understand the vulnerabilities exploited, and simulate attack-defense strategies using real tools. These sessions go beyond theoretical learning and push learners to think like both attackers and defenders.
Participants will build projects around topics like ransomware attack analysis, phishing campaign mitigation, firewall configuration, and endpoint security deployment. These projects not only strengthen technical skills but also demonstrate the learner’s ability to apply knowledge in a job setting, significantly improving employability.
The program is structured to deliver 100+ hours of live instructor-led sessions combined with self-paced labs and project assignments. Learners will also receive career counseling, resume-building support, and interview preparation tailored to cybersecurity roles.
Career Outcomes and Placement Support
By completing the Cyber Security Job Ready Program training in Solapur, learners can aim for high-demand roles such as Security Analyst, SOC Engineer, Ethical Hacker, Penetration Tester, Information Security Consultant, and Cloud Security Specialist. The training is not just about skill development; it is aligned to job market requirements with the goal of full-time placement.
Solapur, although a Tier-II city, is witnessing a rise in IT infrastructure and startups, and the need for cybersecurity professionals is on the rise. Several companies, including IT service providers and manufacturing enterprises in the region, are actively hiring cybersecurity talent. The program ensures that learners from Solapur do not need to relocate to metros to acquire quality training or secure cybersecurity roles.
Moreover, the institute offers a dedicated placement cell that works in tandem with hiring companies and provides continuous job alerts, interview scheduling, and post-training mentorship.
Why Choose SevenMentor for Cyber Security Training?
SevenMentor, the best training institute for Cyber Security Job Ready Program Training, has earned a reputation for its commitment to quality education, industry-oriented pedagogy, and high placement records. With state-of-the-art lab infrastructure, certified trainers, and an extensive support system, SevenMentor stands out as a leader in professional IT training in Solapur.
The training institute offers an immersive learning environment with practical labs, customized training paths, and real-time mentorship. In addition, learners benefit from personalized learning journeys, ensuring that their individual strengths and learning styles are addressed effectively.
What makes SevenMentor particularly valuable is its long-standing association with industry leaders, certification bodies, and cybersecurity communities. These affiliations enrich the course content and provide learners with globally recognized skills. Feedback-driven improvement cycles and post-course support are additional highlights of the training experience.
By enrolling at SevenMentor, the best training institute for Cyber Security Job Ready Program Training, candidates gain more than just a certificate—they become part of a skilled workforce that is capable of defending critical digital assets in today’s cyber warzone.
Training Infrastructure and Learning Experience
SevenMentor provides a blended learning infrastructure that ensures consistency across in-person and remote training experiences. The Solapur facility is equipped with modern labs, high-speed internet, cybersecurity simulators, and digital classrooms that enable seamless and effective learning.
A Learning Management System (LMS) is also provided to all learners, which hosts recorded sessions, assignments, downloadable resources, and mock tests. Learners can revisit sessions, submit projects, and communicate with mentors via the platform, fostering a collaborative and flexible learning environment.
The Solapur center maintains a strong faculty-to-student ratio, ensuring that each learner receives personalized attention. Regular doubt-solving sessions, interactive discussions, and peer learning are part of the culture, making the overall experience deeply engaging and rewarding.
Certifications and Global Recognition
The Cyber Security Job Ready Program Courses in Solapur are aligned with international standards and help prepare learners for globally recognized certifications such as: EC-Council Certified Ethical Hacker (CEH), CompTIA Security+, CISSP (Certified Information Systems Security Professional), OSCP (Offensive Security Certified Professional), CISM and CISA.
These certifications are highly sought after by employers and significantly increase the credibility and market value of the learners. The course provides ample guidance and exam preparation support to help learners clear these certifications with confidence.
Cybersecurity is no longer an optional skill—it is a vital part of any modern IT or business strategy. For professionals and freshers in Solapur aspiring to enter this lucrative and essential field, the Cyber Security Job Ready Program Classes in Solapur offer an unbeatable opportunity. With a curriculum rooted in real-world applications, a pedagogy designed by industry leaders, and an infrastructure that supports immersive learning, this program is an ideal launchpad for a successful cybersecurity career.
Online Classes
SevenMentor also offers interactive and in-depth online Cyber Security Job Ready Program classes in Solapur. Interactive live sessions, virtual labs, and real-time mentorship are integral components of the online experience. The sessions are conducted by the same industry-certified trainers who lead the classroom programs. Learners also receive full access to the Learning Management System (LMS), allowing them to review lectures, submit assignments, and interact with instructors on their own schedule.
This mode of learning ensures that geographical limitations do not hinder career growth in cybersecurity. Online learners receive full placement support and certification guidance, just like their classroom counterparts. With flexible timings, recorded sessions, and weekend batches, the online training module is especially advantageous for those balancing work or academics alongside their learning journey.
Corporate Training
SevenMentor offers customized corporate Cyber Security Job Ready Program Courses in Solapur are tailored to address enterprise-specific challenges, compliance requirements, and workforce upskilling goals.
SevenMentor corporate training packages that include on-site sessions, remote learning options, and customized modules based on industry verticals such as BFSI, healthcare, IT services, and manufacturing. The corporate curriculum covers end-to-end cybersecurity lifecycle topics and is delivered by experts with experience in enterprise security operations.
Enterprises benefit from custom assessments, post-training performance analysis, and cybersecurity readiness evaluations. By partnering with SevenMentor, the best training institute for Cyber Security Job Ready Program Training, companies can ensure their teams are not only trained but are also capable of defending critical systems from cyber threats.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)