About Cyber Security
In an era where digital transformation governs nearly every sector, cybersecurity has emerged as a critical need across industries. With a drastic surge in cyberattacks, ransomware threats, phishing scams, and data breaches, companies worldwide are focusing more than ever on strengthening their digital defenses. This rise in cybersecurity awareness has significantly increased the demand for skilled cybersecurity professionals. Responding to this growing need, Cyber Security Job Ready Program Classes in Sambhajinagar by SevenMentor have become a beacon for aspirants who seek to establish a rewarding and future-proof career in cybersecurity.
The Importance of Cybersecurity in the Modern World
The digital ecology of today is vast and ever-changing. The attack surface has grown as IoT, cloud computing, artificial intelligence, and big data have become more integrated into daily operations. Unauthorised access, data manipulation, and service interruptions are just a few of the vulnerabilities that businesses face today. Sensitive data protection is becoming not only a technical issue but also a business-critical one.
Cybersecurity now demands a highly skilled workforce equipped with the ability to detect vulnerabilities, respond to incidents, manage risks, and maintain compliance. It is no longer limited to IT departments but has found relevance in finance, healthcare, education, and government sectors. With these dynamics, professionals trained through Cyber Security Job Ready Program training in Sambhajinagar are becoming indispensable assets to any organization aiming to safeguard its digital infrastructure.
Why Choose the Cyber Security Job Ready Program?
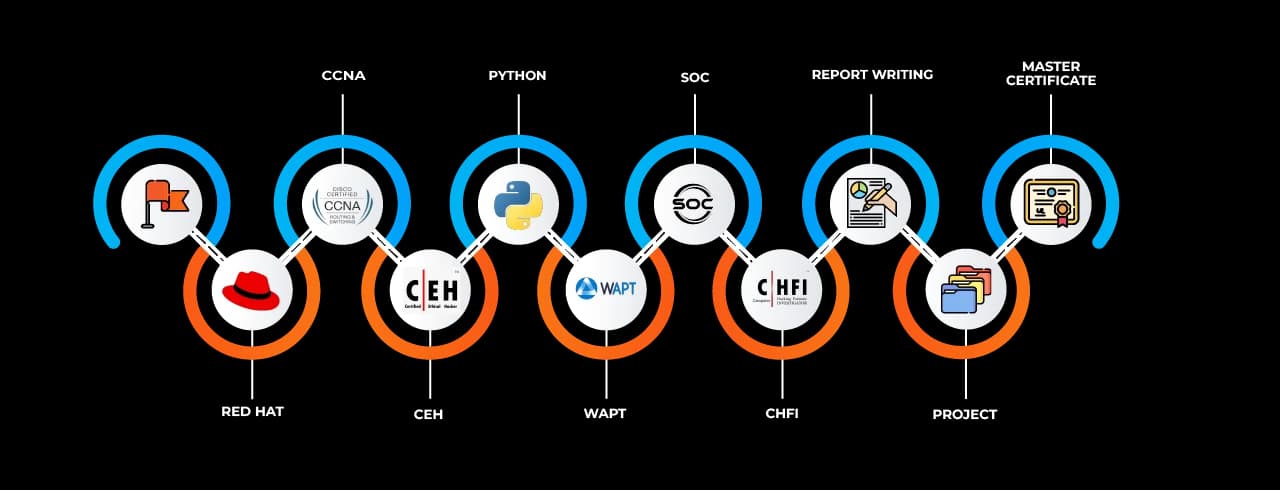
All of the fundamental areas of cybersecurity are covered in the carefully planned Cyber Security Job Ready Program. Network security, ethical hacking, risk assessment, incident response, cloud security, governance, and compliance frameworks are among the fundamental ideas it gives students. Additionally, through labs, simulations, and real-world use cases, the course guarantees that students have practical experience.
SevenMentor, the best training institute for Cyber Security Job Ready Program Training, delivers this program in Sambhajinagar with a focus on developing job-ready skills. Unlike conventional theoretical courses, this program emphasizes practical exposure and industry-relevant techniques. The course is aligned with current industry demands and emerging threats in the cybersecurity landscape. It serves both freshers aiming to start their cybersecurity journey and professionals seeking upskilling opportunities.
Training Structure and Curriculum Overview
The Cyber Security Job Ready Program at SevenMentor follows a step-by-step learning methodology. The program begins with foundational modules such as introduction to cybersecurity, basics of networking, and Linux administration. These modules set the ground for advanced concepts like cryptography, secure software development, malware analysis, and penetration testing.
Special emphasis is placed on learning cybersecurity tools and platforms such as Wireshark, Kali Linux, Metasploit, Nessus, Burp Suite, and Splunk. Learners gain exposure to threat modeling techniques, SOC operations, digital forensics, and cloud security services like AWS Shield, Azure Security Center, and Google Chronicle.
The program ends with capstone projects that test the learner’s ability to design and implement end-to-end cybersecurity solutions. These projects simulate real-world challenges and are mentored by seasoned cybersecurity professionals with years of industry expertise. As a result, students completing the Cyber Security Job Ready Program Classes in Sambhajinagar are industry-prepared and confident to take on roles such as Security Analyst, SOC Specialist, Ethical Hacker, and Incident Responder.
Faculty and Industry Alignment
The quality of trainers directly impacts the effectiveness of a technical course. The Cyber Security Job Ready Program at SevenMentor is led by certified professionals who have deep domain knowledge and real-world implementation experience. These instructors hold credentials such as CEH, CISSP, CompTIA Security+, and CISM, and bring with them insights from working with top-tier MNCs and government institutions.
The faculty members ensure learners not only understand the theoretical frameworks but also gain the ability to implement them in practical scenarios. Through mentorship, guidance, and continuous performance evaluation, students can monitor their growth and readiness for job roles in cybersecurity.
Industry alignment is a key focus of the program. The training curriculum is regularly updated to incorporate current threat intelligence trends, new compliance regulations like GDPR and ISO 27001, and innovations in cybersecurity technologies. This real-time synchronization ensures that learners of the Cyber Security Job Ready Program courses in Sambhajinagar are always a step ahead of industry expectations.
Hands-On Labs and Simulation Exercises
One of the core differentiators of this program is its emphasis on experiential learning. The program includes access to virtual labs that simulate real attack scenarios in a controlled environment. These labs help learners understand attacker behaviors, exploit vulnerabilities, and defend systems under live conditions. The exercises are carefully designed to promote critical thinking, logical reasoning, and efficient incident handling.
Simulated red team vs. blue team exercises prepare students for real-time adversarial engagements. Through these simulations, students understand the importance of teamwork, communication, and coordinated response, which are vital for any Security Operations Center (SOC).
By the end of the course, students would have built an extensive practical portfolio that demonstrates their cybersecurity capabilities—making them strong candidates in a competitive job market.
Certifications and Placement Support
The Cyber Security Job Ready Program is also a preparatory platform for multiple globally recognized certifications. Students are trained to clear certifications like CEH (Certified Ethical Hacker), CompTIA Security+, Cisco CyberOps, and more. These certifications add immense value to a candidate’s profile and boost employability in top-tier companies.
Placement support is another strong advantage of enrolling with SevenMentor. The institute has partnered with numerous tech companies, startups, and consulting firms that actively hire cybersecurity talent. From resume-building workshops to mock interviews and job referrals, the support extends throughout the placement journey. Graduates of the Cyber Security Job Ready Program training in Sambhajinagar have been successfully placed in leading cybersecurity and IT firms across India.
Learning Environment and Infrastructure
SevenMentor maintains a student-centric learning environment with well-equipped classrooms, high-speed connectivity, and dedicated lab infrastructure. The Sambhajinagar center is strategically located and easily accessible, providing a professional yet friendly atmosphere conducive to focused learning.
The batch sizes are deliberately kept small to facilitate personalized attention and interactive sessions. The institute also maintains a learning management system (LMS) where students can access recordings, notes, assignments, and quizzes, allowing them to revise and self-assess regularly.
Cybersecurity has evolved into a dynamic and mission-critical domain in today’s digital-first world. The demand for skilled cybersecurity professionals continues to soar, and the gap between industry needs and qualified resources remains significant. With this context, enrolling in Cyber Security Job Ready Program Classes in Sambhajinagar is a strategic move for anyone aiming to build a secure, rewarding, and high-growth career.
Online Classes
SevenMentor also offers online Cyber Security Job Ready Program classes. The online classes are designed with the same rigorous standards as the classroom sessions and are conducted by experienced instructors via live interactive sessions.
Online learners gain access to virtual labs, recorded sessions, LMS support, and weekly mentorship—all from the comfort of their location. These sessions ensure real-time communication, query resolution, and practical demonstrations. The flexibility of online training allows working professionals and students with busy schedules to upskill without disrupting their commitments.
Corporate Training
SevenMentor offers corporate Cyber Security Job Ready Program training. Organizations looking to strengthen their internal cybersecurity teams can benefit immensely from custom-designed training modules. These modules are tailored to the company’s technology stack, risk posture, and compliance requirements.
Delivered on-site or virtually, these sessions can cover specific areas like security audits, data privacy regulations, cloud security, or insider threat mitigation. The corporate training offered under the Cyber Security Job Ready Program Classes in Sambhajinagar ensures that organizational teams are trained in the latest technologies and standards while building a culture of cyber resilience.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)