About Cyber Security
In the rapidly evolving digital ecosystem, cyber threats have escalated in complexity, frequency, and severity. As cybercrime continues to rise, businesses, governments, and individuals require professionally trained cybersecurity experts who can secure digital infrastructures effectively. The Cyber Security Job Ready Program Classes in Sangli offer a powerful opportunity for aspiring professionals to build strong foundational knowledge and advanced skills to become future-ready cyber defenders.
The Cyber Security Job Ready Program training in Sangli is structured to provide a robust learning experience that covers both theoretical concepts and hands-on practical exposure. It is perfect for newcomers to the IT field, seasoned pros moving into cybersecurity, and even mid-level IT specialists who want to improve their knowledge of risk management, incident response, network security, cryptography, and ethical hacking. Through use cases and real-world simulations, this course prepares students to identify, evaluate, and eliminate cyberthreats and vulnerabilities.
The focus of this program is to prepare students for immediate job readiness in the domain of cybersecurity. As enterprises in India, especially Tier-2 cities like Sangli, continue to invest in digital transformation and IT infrastructure, the demand for certified cybersecurity professionals is experiencing exponential growth. SevenMentor, recognized as the best training institute for Cyber Security Job Ready Program Training, offers this specialized program with the intent to bridge the industry-academic gap and deliver practical competencies aligned with industry demands.
Comprehensive Curriculum Designed for Real-World Application
The curriculum of the Cyber Security Job Ready Program courses in Sangli at SevenMentor is aligned with global cybersecurity frameworks, such as NIST, ISO/IEC 27001, and OWASP. It starts with the fundamentals of information security and progresses towards advanced cybersecurity modules such as penetration testing, malware analysis, vulnerability management, SIEM tools, endpoint protection, and digital forensics.
Students are introduced to networking and security architectures, operating system security (Windows and Linux), firewalls, IDS/IPS systems, and threat intelligence. Emphasis is placed on understanding attack vectors and threat actor behavior, using red team-blue team simulations to build both offensive and defensive capabilities. Case-based learning enables learners to solve complex problems like ransomware outbreaks, DDoS attacks, insider threats, and cloud security breaches.
A key component of the course is the integration of various tools and technologies used by cybersecurity professionals today. Learners gain hands-on exposure to tools like Wireshark, Nmap, Metasploit, Burp Suite, Nessus, Snort, Splunk, and more. These tools are used to assess system vulnerabilities, conduct reconnaissance, automate scans, analyze logs, and simulate attacks in a secure environment.
Industry-Oriented Training Methodology
The Cyber Security Job Ready Program Classes in Sangli offered by SevenMentor adopt a blended learning approach that includes instructor-led sessions, hands-on labs, assessments, case studies, and live projects. This methodology ensures that learners do not just acquire theoretical knowledge but also develop the capability to implement cybersecurity controls in real-time environments.
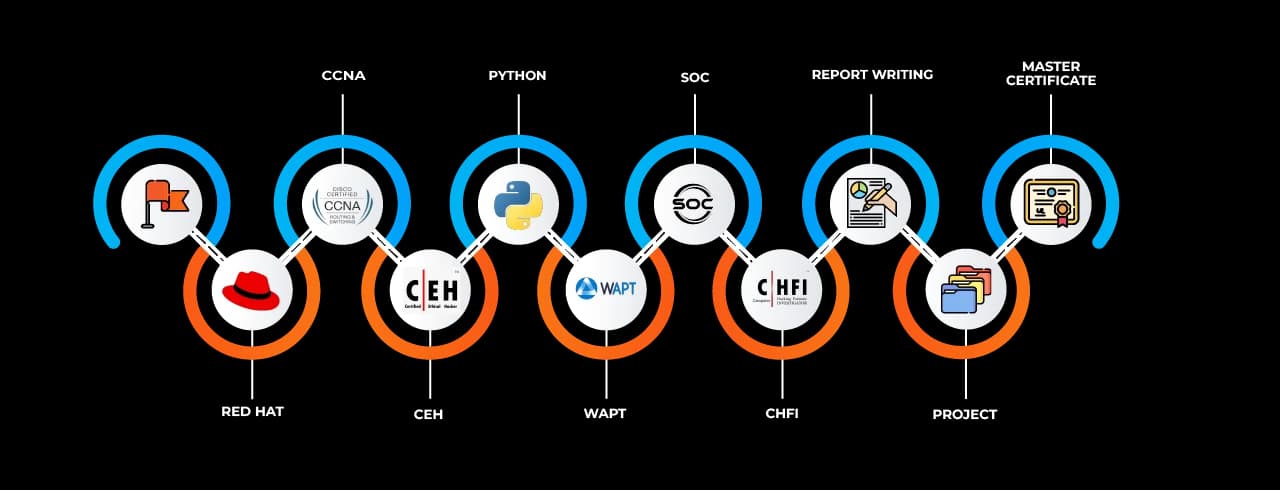
A unique aspect of the training program is its alignment with industry certifications such as CompTIA Security+, CEH (Certified Ethical Hacker), CISSP, and ISO/IEC 27001 Lead Implementer. Learners are prepared to attempt these global certifications, thereby enhancing their employability in both Indian and international job markets. Capstone projects at the end of the course validate the learner’s readiness for cybersecurity roles by simulating real-world security challenges, such as threat hunting, log monitoring, risk assessment, and remediation planning.
Trainers at SevenMentor are certified security experts with extensive industry experience in cyber defense, penetration testing, enterprise risk management, and SOC operations. Their hands-on knowledge is translated into mentorship that helps learners understand real-world issues faced in enterprise environments. As cybersecurity is an ever-evolving domain, trainers also integrate emerging trends such as zero trust architecture, AI in cybersecurity, and DevSecOps into the learning sessions.
Advanced Lab Infrastructure and Learning Resources
One of the highlights of SevenMentor’s Cyber Security Job Ready Program training in Sangli is its state-of-the-art lab infrastructure that allows learners to practice on virtual environments and cyber ranges. The lab is designed to mimic enterprise networks, enabling learners to execute real-world scenarios like reconnaissance, exploitation, privilege escalation, and post-exploitation procedures in a controlled, safe environment.
Virtual labs are accessible 24/7, giving learners the flexibility to continue their practice outside of class hours. Learners are also given access to extensive digital libraries that include e-books, white papers, research articles, and vendor documentation. Recorded lectures, revision modules, and interactive quizzes help reinforce concepts and prepare students for interviews and certification exams.
Career Scope and Job Readiness
Upon completion of the Cyber Security Job Ready Program courses in Sangli, learners are equipped to step into a variety of roles in the cybersecurity domain. These include roles such as Cybersecurity Analyst, Security Operations Center (SOC) Engineer, Penetration Tester, Security Auditor, Malware Analyst, and Network Security Engineer. The job market for these roles is expanding across sectors like BFSI, IT services, e-commerce, healthcare, government, and manufacturing.
This program's practical and industry-focused approach guarantees that students are prepared for the workforce right away. SevenMentor provides soft skills training, resume-building workshops, practice interviews, and help with direct placement. Learners can anticipate interviews with cybersecurity teams from startups and large corporations due to established employment ties with top-tier firms.
By 2025, there will likely be a 1.5 million-person need for cybersecurity specialists in India, as the majority of businesses currently place a higher priority on cyber resilience than compliance. Students who receive training at a reputable institution like SevenMentor are certain to acquire both theoretical understanding and practical knowledge that corresponds with this expanding market demand.
Why Choose SevenMentor?
SevenMentor stands out as the best training institute for Cyber Security Job Ready Program Training in Sangli due to its holistic training approach, updated courseware, and high trainer competence. The institute’s commitment to quality is reflected in its strong placement track record, trainer credentials, and cutting-edge lab facilities. Learners receive personalized guidance throughout the training lifecycle—from the first module to the final placement.
Another important advantage is SevenMentor’s focus on practical experience and real-world problem solving. The institute emphasizes industry-based projects, security assessments, and live simulations to build robust competencies. With dedicated career counseling and lifetime access to learning resources, SevenMentor provides sustained support even after course completion.
In addition to being technically rigorous, the course is designed to be accessible to learners from diverse backgrounds. Whether you’re a fresher in IT, an experienced system administrator, or an engineer looking to specialize in security, the Cyber Security Job Ready Program Classes in Sangli can serve as a launchpad for a successful cybersecurity career.
In today’s digital-first economy, cybersecurity is no longer a specialized function; it is a foundational component of business continuity and national security. Organizations require professionals who not only understand the technical dimensions of security but can also design, implement, and manage end-to-end security frameworks. The Cyber Security Job Ready Program training in Sangli by SevenMentor addresses this industry requirement by producing well-trained, job-ready cybersecurity professionals capable of securing digital assets and reducing risk exposure.
Online Classes
SevenMentor offers interactive online Cyber Security Job Ready Program Classes in Sangli. The online training follows the same rigorous standards as the in-person sessions, with live instructor-led classes, virtual lab access, project-based assessments, and one-on-one mentorship. Learners can attend sessions from the comfort of their homes without compromising on quality or hands-on practice.
The online platform supports recording playback, interactive quizzes, collaborative assignments, and virtual simulation labs. This flexible format enables learners to balance their learning journey with personal and professional commitments. Whether you are based in Sangli or elsewhere, the online delivery mode ensures uninterrupted access to high-quality cybersecurity training.
Corporate Training
SevenMentor offers customized corporate Cyber Security Job Ready Program training. These are tailored to the organization’s risk profile, IT architecture, and compliance requirements. Corporate versions of the Cyber Security Job Ready Program training in Sangli are delivered on-site or virtually, with modules selected based on enterprise needs.
From secure coding practices to endpoint protection and incident response, the corporate training solutions are designed to build cyber resilience within the organization. SevenMentor’s trainers work closely with enterprise stakeholders to align the training objectives with operational goals, ensuring that the workforce is equipped to protect digital assets effectively. Post-training assessments, feedback, and support ensure that the learning outcomes translate into measurable improvements in the organization’s security posture.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)