About Cyber Security
In today’s rapidly evolving digital landscape, the demand for well-trained cyber security professionals is rising steadily. With the frequency and severity of cyber-attacks increasing globally, organizations are investing more in robust security infrastructure and skilled personnel to safeguard their assets. This has led to a significant surge in the need for structured, industry-relevant Cyber Security classes in Australia. To meet this growing need, a number of specialised training institutes are offering complete programs that provide learners with sophisticated security knowledge, practical experience, and globally recognised certificates.
Australia, with its gradual adoption of digital technology, cloud computing, and smart infrastructure, is especially vulnerable to sophisticated cyber assaults. As a result, the nation places a high value on cultivating professional cybersecurity expertise across a variety of sectors. With well-defined curriculum, hands-on lab experiences, and a strong industry connection, Cyber Security courses in Australia are among the most sought-after educational tracks for both aspiring IT professionals and experienced individuals seeking career transformation.
The Rising Importance of Cyber Security in the Australian Economy
Australia has experienced a dramatic shift towards digitization across both public and private sectors. From banking and healthcare to education and defense, data is increasingly stored and transmitted digitally. Consequently, organizations are more exposed to a range of cyber threats including ransomware, phishing, insider threats, and DDoS attacks. This has led to a substantial uptick in investments in information security infrastructure and services.
In response to these developments, educational institutions and training providers are aligning their offerings with global standards and frameworks. Cyber Security training in Australia is no longer limited to theoretical concepts but has evolved into a dynamic, application-focused discipline that prepares individuals to deal with real-world cyber threats. Learners gain exposure to threat modeling, intrusion detection systems, vulnerability assessment tools, encryption mechanisms, network security principles, and ethical hacking methodologies.
This demand is further amplified by regulatory compliance requirements such as the Australian Privacy Act, Essential Eight mitigation strategies, and international standards like ISO 27001. Companies need trained professionals who not only understand these regulations but can also implement them effectively. Therefore, enrolling in Cyber Security classes in Australia is now considered a strategic career move for those aiming to stay ahead in the IT domain.
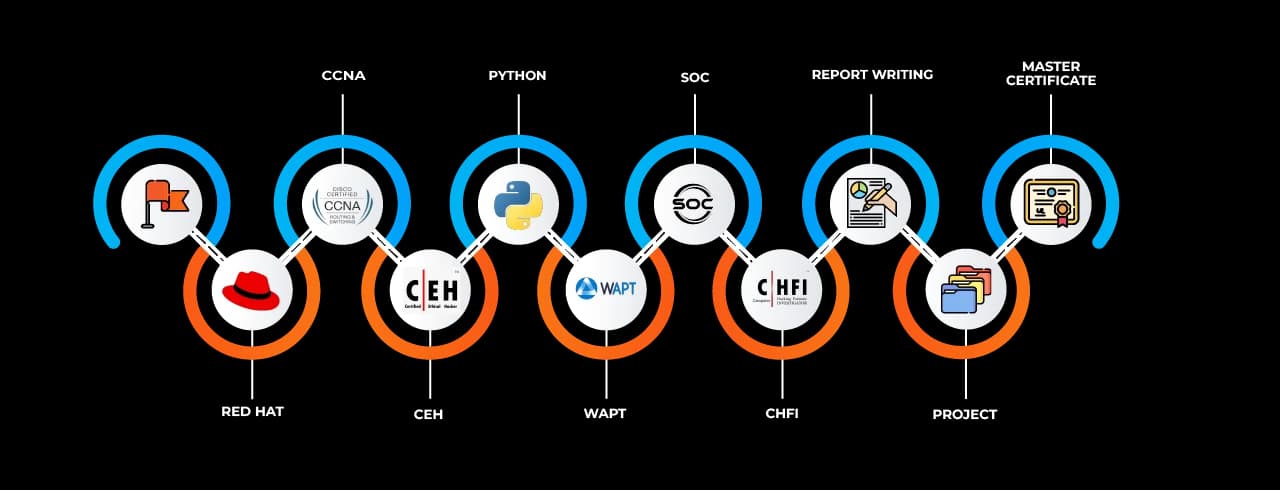
Curriculum and Learning Pathways
The curriculum of Cyber Security courses in Australia is carefully structured to cater to a wide spectrum of learners—from absolute beginners to seasoned IT professionals. Foundational lessons include fundamental concepts such computer networks, operating systems, and threat detection. Learners proceed to more complex topics such as penetration testing, cloud security, cryptography, incident response, malware analysis, and risk management.
Simulations, lab activities, and real-world case studies are also used in the courses to provide hands-on instruction. Working on simulated cyber-attack scenarios provides learners with practical experience managing security breaches and responding to incidents. Several institutes now provide virtual labs, which allow students to practise their abilities in a safe environment without the risk of real-world consequences.
One of the standout features of top-tier Cyber Security training in Australia is its alignment with industry certifications. Learners are guided through the preparation process for globally recognized credentials such as CompTIA Security+, CEH (Certified Ethical Hacker), CISSP (Certified Information Systems Security Professional), and CISM (Certified Information Security Manager). These certifications not only validate the learner's knowledge but also enhance their employability in competitive job markets.
Career Opportunities and Industry Demand
Graduates of Cyber Security courses in Australia are well-positioned to enter a range of high-demand roles including security analyst, penetration tester, security consultant, network security engineer, and cyber threat intelligence analyst. With cybercrime projected to cost the world over $10 trillion annually by 2025, businesses are willing to pay a premium for skilled security professionals.
Australia's tech hotspots, including Sydney, Melbourne, Brisbane, and Perth, are constantly looking for cybersecurity skills. Furthermore, the federal government and military organisations are increasing their digital defence infrastructure, which will open up new employment opportunities. Whether it's securing financial systems, key infrastructure, or preventing data breaches in healthcare systems, cybersecurity specialists are at the forefront of organisational defence measures.
Moreover, startups and small businesses are also realizing the importance of cybersecurity. As a result, there’s a growing trend of hiring part-time or freelance security consultants. This opens up flexible work opportunities for trained professionals who may want to pursue consulting, remote roles, or freelance gigs after completing Cyber Security classes in Australia.
Why Choose SevenMentor for Cyber Security Training
Among the many institutes offering cybersecurity education, SevenMentor the best training institute for Cyber Security Training stands out for its commitment to excellence, practical focus, and industry-driven pedagogy. With a track record of successfully training thousands of IT professionals, SevenMentor has positioned itself as a premier institution delivering robust, career-oriented training.
The curriculum at SevenMentor is regularly updated to reflect the latest developments in threat intelligence, ethical hacking tools, security frameworks, and governance models. Each course is taught by certified instructors with significant industry experience, ensuring learners gain insights that go beyond textbooks. Real-time labs and projects enable students to apply theoretical concepts in realistic settings.
Another hallmark of SevenMentor is its placement support and mentorship. The institute maintains a strong network with IT firms across Australia and beyond, helping learners secure job opportunities upon successful completion of their training. Whether you are starting your career or seeking to move into a specialized role in cybersecurity, SevenMentor provides a structured, supportive path to success.
Choosing SevenMentor the best training institute for Cyber Security Training ensures that learners gain not only academic knowledge but also the practical and strategic skills needed to thrive in this evolving domain. Their reputation for delivering high-quality education, along with student-centric services, makes them a preferred choice for Cyber
Security courses in Australia.
The world is facing an unprecedented level of cyber threats, making the need for skilled professionals more urgent than ever. In Australia, where digital transformation is accelerating across all sectors, cybersecurity is not just an IT concern—it’s a business imperative. Investing in Cyber Security classes in Australia is therefore a wise and forward-looking decision for individuals aiming to build or pivot their careers.
By enrolling in well-structured and industry-aligned Cyber Security courses in Australia, learners gain not only foundational knowledge but also the advanced technical acumen required to tackle modern cyber threats. Practical training, certification preparation, and strong industry integration make these courses highly valuable in the current job market.
Online Classes
SevenMentor offers online Cyber Security training in Australia. These online sessions are led by experienced trainers who deliver live lectures, engage in Q&A sessions, and provide personalized feedback. The online format retains all the core benefits of classroom learning, including lab access, assignments, and project-based assessments.
One of the main advantages of online training is flexibility. Learners can access content from anywhere, allowing them to balance studies with professional or personal commitments. All course materials, including recorded sessions and practice labs, are accessible through a centralized learning management system. This mode of delivery is ideal for working professionals or international students seeking to benefit from Australian expertise in cybersecurity.
Corporate Training
SevenMentor also offers customized corporate Cyber Security training in Australia. These programs are tailored to meet the specific needs of businesses—whether it's upskilling IT staff, preparing for compliance audits, or training employees to detect phishing attempts.
SevenMentor offers corporate training packages that include on-site workshops, online modules, and blended learning solutions. Delivered by expert instructors, the sessions are structured to align with organizational goals, industry standards, and the current threat landscape. Employees not only learn the technical aspects of cybersecurity but also develop a culture of security awareness that benefits the entire organization.
By investing in corporate Cyber Security classes in Australia, businesses can significantly reduce their vulnerability to attacks, ensure compliance with legal regulations, and build a robust, security-aware workforce.
 A comprehensive cybersecurity strategy has numerous layers of protection.
A comprehensive cybersecurity strategy has numerous layers of protection.  Prevention of cyber attacks is the primary goal of a Cyber expert.
Prevention of cyber attacks is the primary goal of a Cyber expert. An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.
An organization's people, processes, and technology must complement one another to effectively defend against cyber threats.-1744728435835.webp&w=3840&q=85)