About Web Application Penetration Testing
In an age of digital transformation, web applications have evolved into vital interfaces for organisations, governments, and individuals. With the growing reliance on digital platforms, the frequency and sophistication of cyber threats attacking them has increased. To protect these digital assets, Web Application Penetration Testing has evolved as a critical discipline in the cybersecurity field. Australia, as a growing hub for technology and industry, is experiencing an increase in demand for talented professionals in this field. Through comprehensive Web Application Penetration Testing Classes in Australia, learners can acquire the expertise to identify vulnerabilities, exploit weaknesses, and secure applications against real-world attacks.
Understanding the Core of Web Application Penetration Testing
Web Application Penetration Testing is a structured method that evaluates the security posture of web applications. It entails simulating attacks on a web system to identify exploitable flaws before hostile actors do. The testing not only looks for recognised concerns like as SQL injection, Cross-Site Scripting (XSS), and authentication flaws, but also for logic mistakes and business logic vulnerabilities.
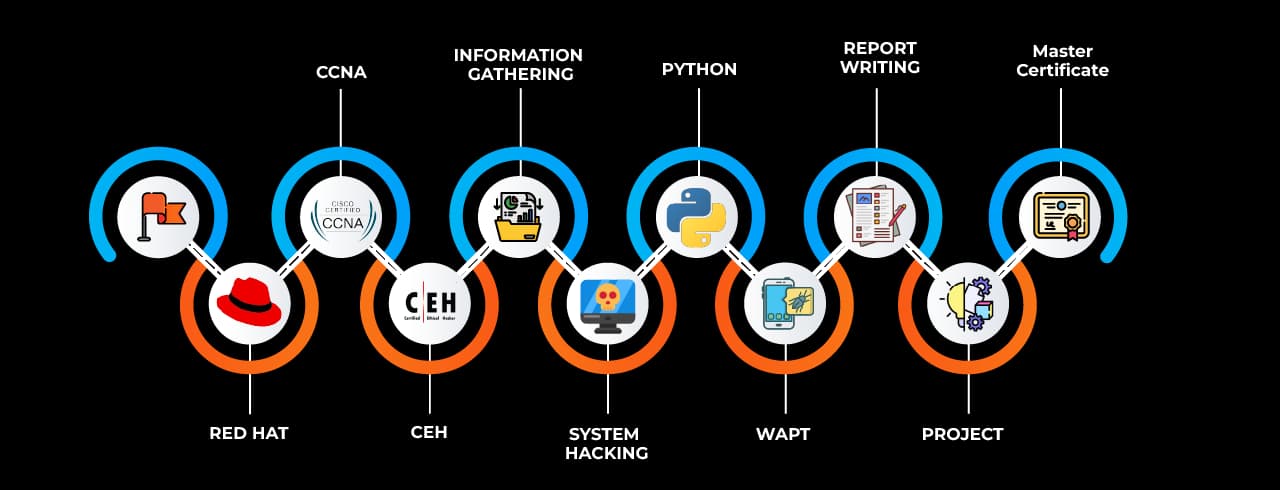
Professionals who undergo Web Application Penetration Testing training in Australia are taught how to mimic the strategies of cyber adversaries while maintaining ethical boundaries. They are trained to utilize manual testing techniques along with automated tools like Burp Suite, OWASP ZAP, and Nikto to evaluate application resilience.
The training curriculum often includes lessons on HTTP protocol analysis, session management, authentication bypass, API testing, cryptography implementations, and SDLC integration. These abilities are essential for those working in security operations, software development, quality assurance, and IT audits.
Technical Skill Development Through Hands-On Labs
The effectiveness of penetration testing education lies in practical exposure. Web Application Penetration Testing courses in Australia at SevenMentor ensure a lab-oriented approach, where theoretical learning is backed by real-world scenarios. Students gain hands-on experience in Conducting black-box, white-box, and grey-box testing, Analyzing HTTP requests and responses, Manipulating parameters to exploit logic flaws, Performing reconnaissance and threat modeling, Crafting custom payloads for XSS and command injection.
These hands-on labs are designed to simulate real-time enterprise environments while teaching students how to tackle modern web frameworks, APIs, and microservices architecture with a security-first perspective. The ability to detect vulnerabilities in single-page applications (SPAs), AJAX-based systems, and RESTful services is critical in today's application security environment.
Curriculum Aligned with International Security Standards
SevenMentor prepares individuals to align their testing methodologies with internationally recognized standards and frameworks such as the OWASP Top 10, ISO/IEC 27001, NIST 800-115, and PCI-DSS. Students are trained to craft detailed penetration testing reports, provide effective risk communication to stakeholders, and recommend prioritized mitigations.
By attending Web Application Penetration Testing Classes in Australia, learners not only develop technical skills but also gain a deep understanding of regulatory compliance, risk assessment, and secure development methodologies. The classes emphasize ethical responsibility, legal considerations, and coordinated vulnerability disclosure processes, making learners job-ready for global opportunities.
Real-Time Threat Simulation and Red Teaming
Penetration testing classes that imitate real-time threat settings offer an excellent training ground. These simulations are intended to represent current attack routes used by cybercriminals and advanced persistent threats (APTs). Learners are introduced to adversarial tactics, methods, and procedures (TTPs) that are commonly utilised in professional red teaming and ethical hacking.
Participants will learn how to model threats, enumerate vulnerabilities, exploit web servers, overcome security restrictions, and escalate privileges in isolated test settings. These simulations help to improve critical thinking and adaptive abilities, which are essential in a continually shifting threat context.
Custom susceptible applications, bug reward programs, and capture-the-flag (CTF) activities are also used during training to strengthen participants' penetration testing abilities. This is especially relevant for security analysts and ethical hackers who want to improve their real-world offensive security skills.
Career Pathways and Industry Demand in Australia
Australia's commitment to improving national cybersecurity capabilities has resulted in an increase in demand for qualified application security specialists. Finance, healthcare, e-commerce, and government institutions are all actively looking for penetration testers to protect their customers' data and digital assets.
Completing Web Application Penetration Testing training in Australia at SevenMentor opens up several career avenues, such Application Security Analyst, Penetration Tester,
Red Team Operator, Security Consultant, DevSecOps Engineer.
The course serves as a springboard to specialised certifications such as Offensive Security Web Expert (OSWE), Certified Ethical Hacker (CEH), GIAC Web Application Penetration Tester (GWAPT), and others. These qualifications are widely recognised around the world and frequently lead to overseas postings and remote work possibilities.
Why SevenMentor for Web Application Penetration Testing Training?
SevenMentor, the best training institute for Web Application Penetration Testing Training, stands out for its expert-led instruction, updated syllabus, and real-world focus.
The institute's courses are designed by industry experts in ethical hacking, red teaming, and safe software development. Their rigorous training path ensures that both novices and seasoned IT professionals understand ideas ranging from basic vulnerabilities to complicated application security designs.
SevenMentor focusses on hands-on laboratories, regular assessments, personalised mentorship, and mock interviews. Learners get access to cloud-based virtual laboratories that simulate real infrastructure vulnerabilities. Furthermore, trainers help students create professional-grade testing results and outstanding portfolios that may be shown to potential employers.
With flexible schedules, comprehensive learning materials, and a supportive learning environment, SevenMentor ensures that aspirants in Australia receive world-class education in a niche but in-demand skillset.
Industry Collaboration and Capstone Projects
To bridge the academic-industry gap, many institutions collaborate with cybersecurity firms, software companies, and government agencies. SevenMentor’s Web Application Penetration Testing Courses in Australia provide capstone projects and internships, where students can apply their knowledge in real business environments.
These projects require students to audit live web applications, conduct end-to-end penetration testing, and generate actionable results. This exposure improves individuals' technical expertise and communication abilities, qualifying them for consulting and client-facing employment.
The incorporation of project-based learning into the curriculum not only confirms a student's capacity to work on real-world challenges, but it also improves employability by demonstrating practical experience.
Building a Community of Ethical Hackers
Penetration testing is more than simply tools and strategies; it's about belonging to a community that values security, transparency, and ethical behaviour. Training institutes urge students to join ethical hacking forums, contribute to open-source security tools, and report flaws through responsible disclosure channels.
Alumni of SevenMentor’s Web Application Penetration Testing Classes in Australia often continue to contribute to security communities such as Bugcrowd, HackerOne, OWASP chapters, and DEF CON groups. These associations provide a continuous learning loop and networking opportunities for professionals in the field.
Enrolling in structured Web Application Penetration Testing Classes in Australia not only equips learners with critical offensive security skills but also makes them valuable assets in the broader cybersecurity ecosystem.
From foundational learning to advanced exploitation techniques, from real-time threat simulations to industry-aligned projects, the journey through a structured training path is transformative. With dedicated institutions like SevenMentor the best training institute for Web Application Penetration Testing Training, learners are assured of comprehensive, up-to-date, and practical education in application security.
Online Course
SevenMentor also offers comprehensive online Web Application Penetration Testing Courses in Australia are now extensively available online. These virtual classes maintain the same rigor as in-person sessions. Students can attend live sessions, access virtual labs, and interact with mentors through learning management systems (LMS).
SevenMentor’s online training programs stand out due to their hands-on nature, weekly challenges, recorded sessions, and instant mentor feedback. Learners can pace their learning while balancing work or academic commitments. The virtual labs provided mirror real-world attack surfaces and allowed learners to practice without requiring any installation or configuration. This accessibility makes the training ideal for working professionals, students, and IT teams across regions.
Corporate Training
SevenMentor offers customized corporate Web Application Penetration Testing training in Australia that is tailored to company-specific needs. Corporate training by SevenMentor involves curriculum customization, on-premise or online delivery, pre-assessments, and post-training evaluation.
Whether it's a development team looking to implement DevSecOps, or a QA team aiming to incorporate security into testing workflows, the corporate training modules are scalable, focused, and outcome-driven. The programs help organizations minimize security risks, reduce technical debt, and maintain compliance with local and international regulations.
 Master Web Application Penetration Testing with Industry Expert Trainers
Master Web Application Penetration Testing with Industry Expert Trainers Learn Advanced Security Techniques to Identify and Exploit Web Vulnerabilities.
Learn Advanced Security Techniques to Identify and Exploit Web Vulnerabilities. Boost Your Cybersecurity Career with SevenMentor’s Hands-On WAPT Training.
Boost Your Cybersecurity Career with SevenMentor’s Hands-On WAPT Training.